ASEAN Mustang Panda
Executive Summary
The program executes “office.exe” with various command lines and parent processes from the "C:\Users\Public\Desktop" directory. It also runs "GetCurrentDeploy.dll" and writes values to the registry. While legitimate programs might use similar actions for file execution and registry updates, malicious software could also use these processes to execute harmful files or modify settings for persistence or evasion. The specific registry actions may indicate malicious behavior. Further analysis is required to assess the intent and nature of the process.
Case Details
Sample information
| Attribute | Details |
|---|---|
| File name | ASEAN Notes.iso |
| File size | 588 KB |
| File type | Disc Image File (ISO) |
| MD5 | 9832bd120aa506758b3c1850dc2f7e41 |
| SHA1 | 8e7dfe85c00f76c2525b0ea001b735b1240f3342 |
| SHA256 | a00673e35eaccf494977f4e9a957d5820a20fe6b589c796f9085a0271e8c380c |
| Attribute | Details |
|---|---|
| File name | ASEAN 2024.lnk, MS.lnk, Mofa memo.lnk |
| File size | 2 KB |
| File type | Shortcut (LNK) |
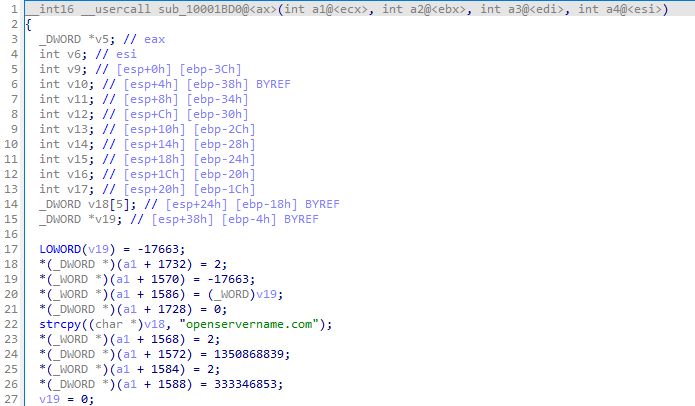
| MD5 | b1c2cac5b573523a0394b82c2e097077 |
| SHA1 | e27a237acb643391a7a5d6c57bd882e4ac72bdb0 |
| SHA256 | d66ab44e898c909d0e2a8b8bbe2eb47dfb76af4962ede47d63477a0f8fcfef23 |
| Attribute | Details |
|---|---|
| File name | NS.lnk |
| File size | 2 KB |
| File type | Shortcut (LNK) |
| MD5 | 698382d42978ee9b86046682cacc76ab |
| SHA1 | dd149a0c4a650df907557b3c0219fde81d339d11 |
| SHA256 | e537c5da268c6a08d6e94d570e8efb17d0ca3f4013e221fadc4e0b3191499767 |
| Attribute | Details |
|---|---|
| File name | GetCurrentDeploy.dll |
| File size | 96 KB |
| File type | Application Extension (DLL) |
| MD5 | d901af6c326d9d6934d818beef214e81 |
| SHA1 | b78e786091f017510b44137961f3074fe7d5f950 |
| SHA256 | 51d89afe0a49a3abf88ed6f032e4f0a83949fc44489fc7b45c860020f905c9d |
Case Specific Requirements
Machine
Windows EnvironmentTools Used
- Floss
- IDA
- ProcMon
- DiffView
- Wireshark
- Fakenet
Static Analysis
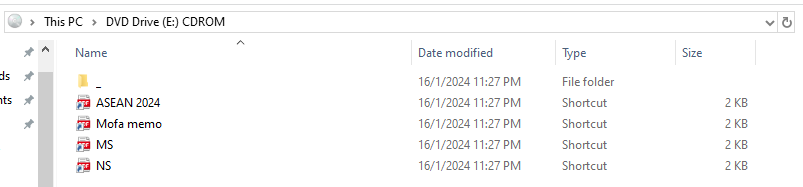
The file was first received as a Disc (.ISO). After opening the ISO, four shortcut PDFs were found:
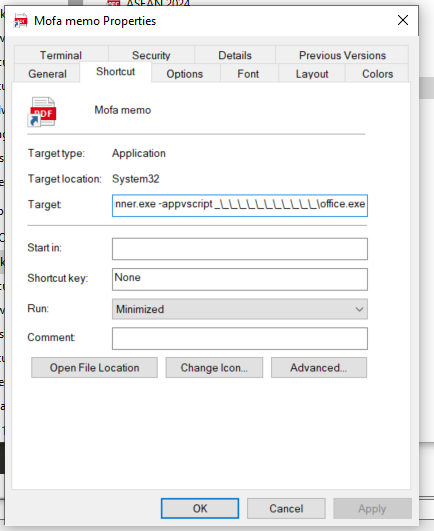
Checking one of the shortcut files shows the target command:
Target command executed:
1
C:\Windows\System32\ScriptRunner.exe -appvscript _\_\_\_\_\_\_\_\_\_\_\_\office.exe
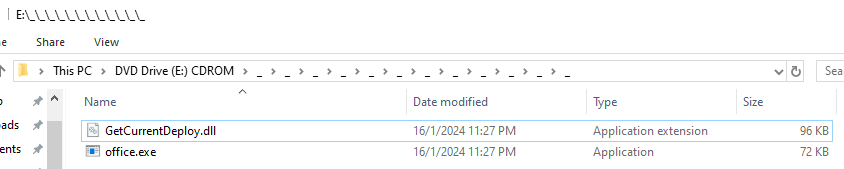
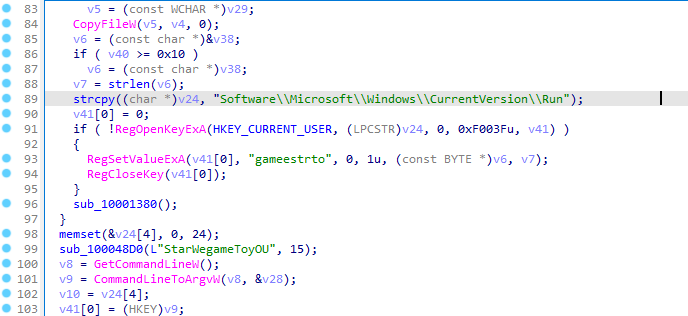
Upon inspecting the folder, two files were found. The office.exe file was not malicious when checked via hash, but the GetCurrentDeploy.dll is.
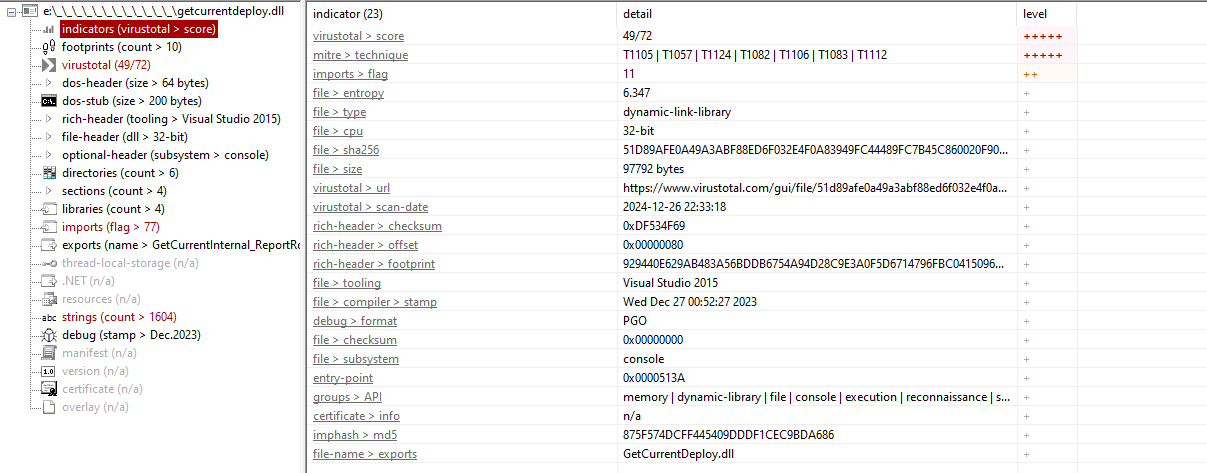
Using PEStudio to analyze the file content:
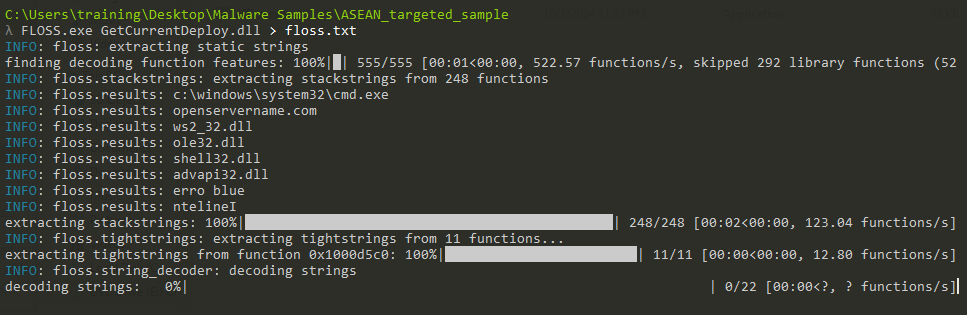
Next, Floss was used to extract the content.
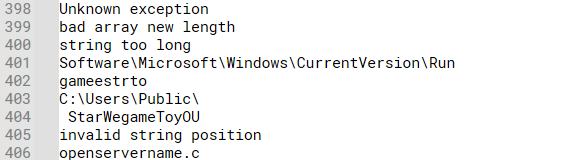
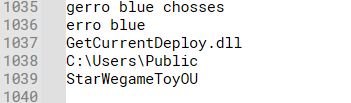
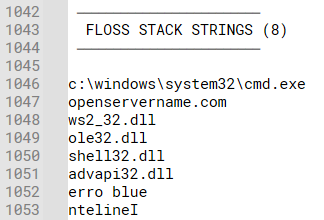
Content inside floss:
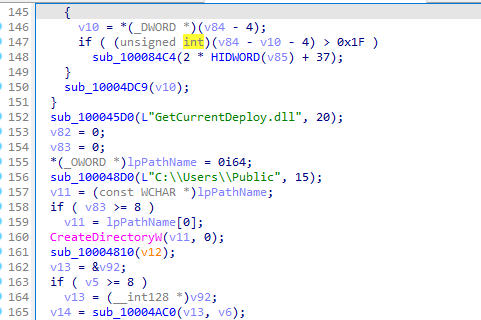
The extracted functions from IDA were analyzed:
Dynamic Analysis
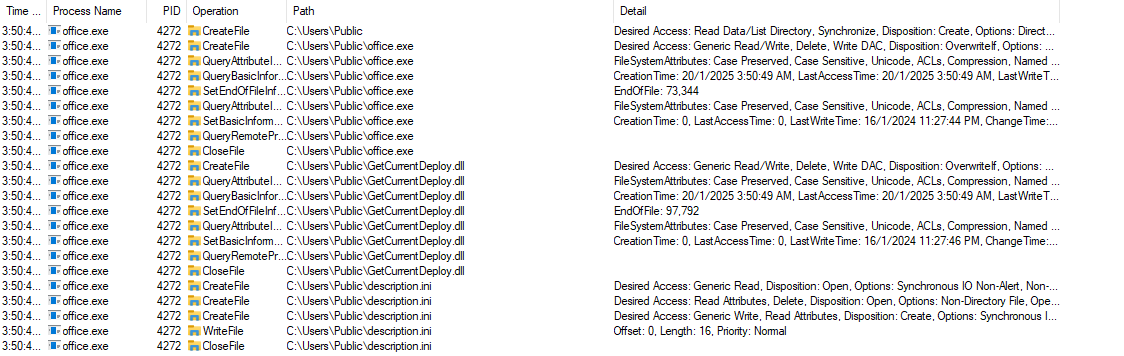
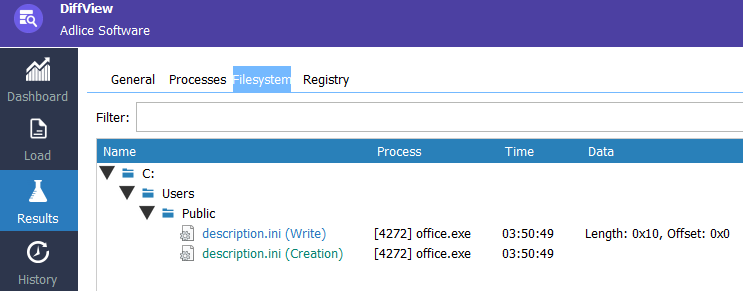
Using ProcMon, we observe the CreateFile and WriteFile actions being executed under the Public directory.
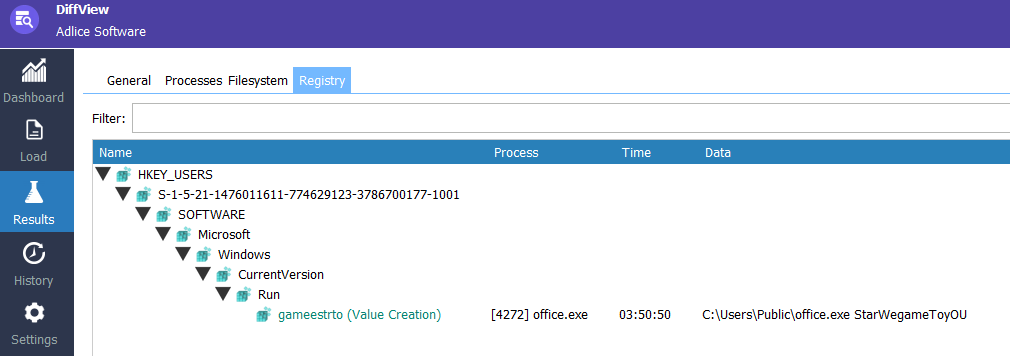
Using DiffView, any interesting changes were monitored.
It shows the registry entries being set for auto-execution during boot.
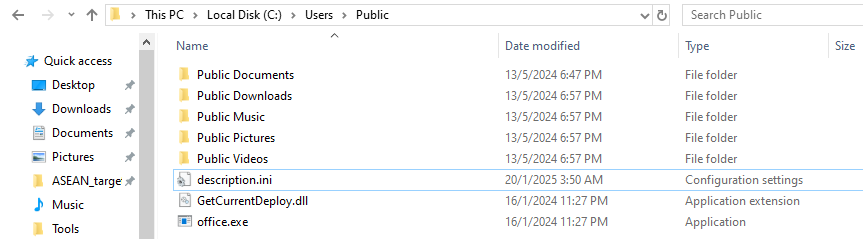
To confirm file creation, the directory was checked and both office.exe and GetCurrentDeploy.dll were found present.
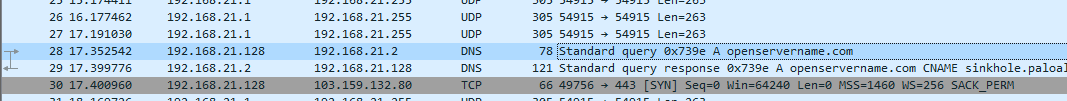
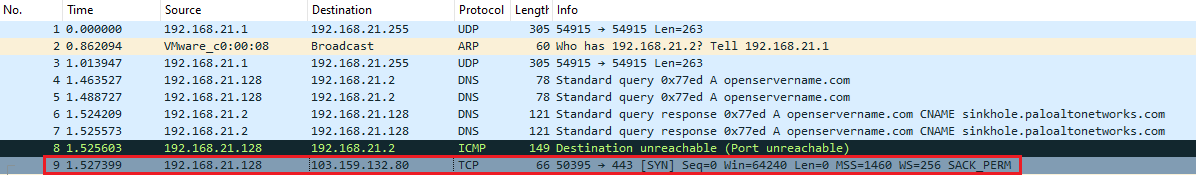
Starting the Wireshark to see any connections was made by this malicious:
Image above we get to see the openservername[.]com attempt to connect with the machine. The following ip also establishes as TCP to the destination of 103[.]159[.]132[.]80:
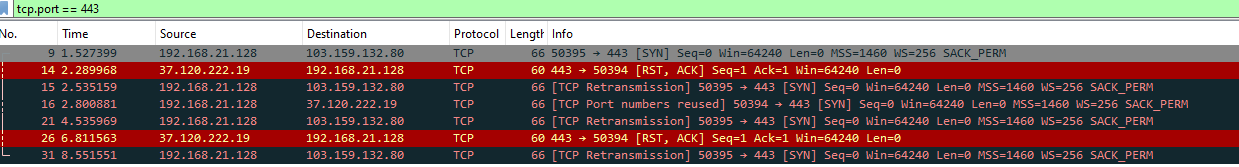
Filtering the TCP Port of 443 and get to see the ip above had a connect with the machine IP.
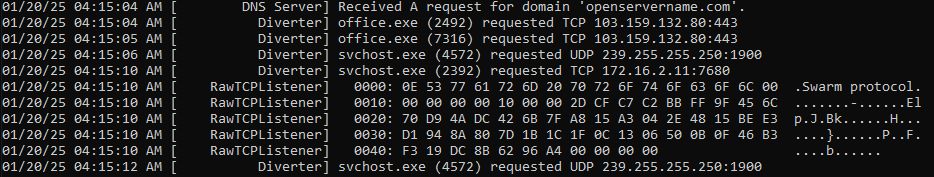
Using Fakenet to monitor the traffic and the TCP comes from office.exe:
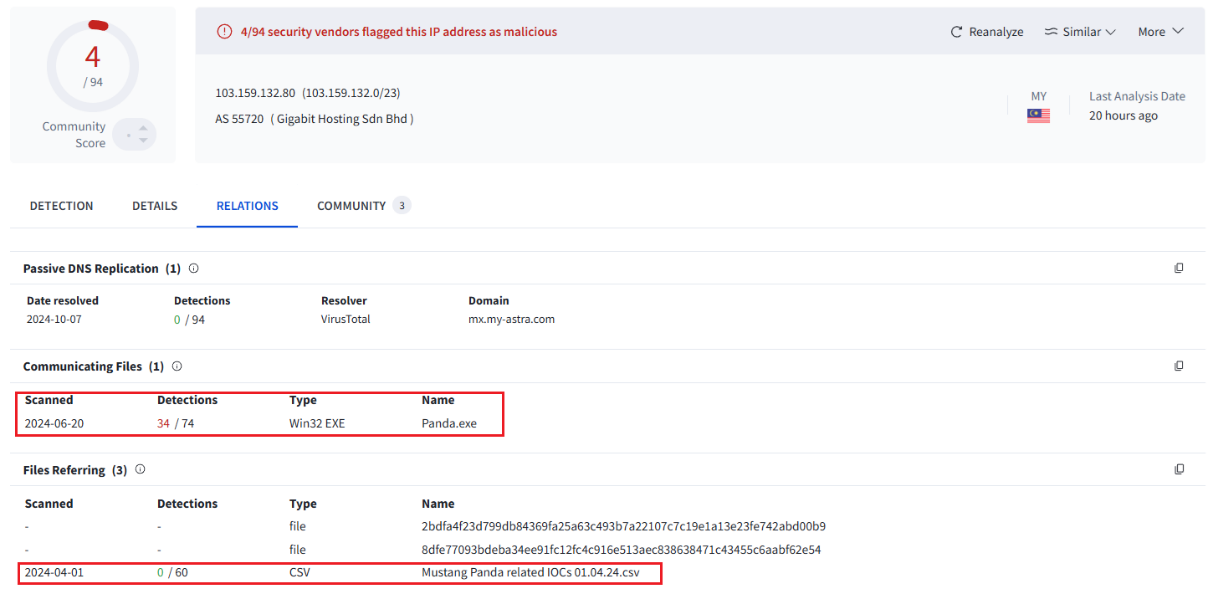
Checking the Relations of those ip on Virustotal have the relation with the panda malware:
Indicators of Compromise (IOCs)
| IOC | Type |
|---|---|
| openservername[.]com | URL |
| 103[.]159[.]132[.]80[:443] | IP:Port |
| HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN\GAMEESTRTO | Registry |
| C:\Users\Public\office.exe | File |
| C:\Users\Public\GetCurrentDeploy.dll | File |
Additional Notes
SHA256 hash of the malicious ISO file
a00673e35eaccf494977f4e9a957d5820a20fe6b589c796f9085a0271e8c380cFull command line configured in one of the malicious shortcuts in the ISO file
C:\Windows\System32\ScriptRunner.exe -appvscript _\_\_\_\_\_\_\_\_\_\_\_\office.exeDomain name found in the sample
openservername.comFull path, including the filename, to which the malware copies itself
C:\Users\Public\GetCurrentDeploy.dllRegistry key name created by the malware
gameestrtoParameters string required for the malware to execute after the initial infection
StarWegameToyOUHosting provider used by the threat actor for their C2 server
Gigabit Hosting Sdn Bhd